SIEM Content Management
SIEM Content includes following: 1. Parsers & Schemas
- Detection Rules
- Workbooks
- Playbooks
- Watchlists
- Threat Hunting
- Automation Rules
It is advised to maintain consistency and centralized management of content by using infrastructure as a code (IaC) methods.
In order to deploy these content items via IaC methodology, we need to pass arguments to configuration files during deployment via Infrastructure-live directory.
You can find all the content available to use in infrastructure-modules/azure/content directory.
Parsers & Schemas
:eyes: Note : Some of the content like schemas, parsers and standard workbooks are deployed by default in every infrastructure.
Detection Rules & Rule Packs
You can deploy rules either by using name of rules or by adding rule pack name in configuration file shared in below file path and then running the update environment script.
File Path
infrastructure-live/azure/.template/resource-groups/security-log-analytics/services/sentinel-rules/config.tpl.hclYou can add the file name that you want to deploy as shown in below example:
inputs = {
# For pre packed rule sets for any log source, use rule_packs.
rule_packs = [
"windows/windows-sysmon-pack",
]
# For individual rules, add rule paths from content directory.
additional_rules = [
"ioc/security/sysmon/a-variant-of-data-stealer-trojan-activity",
"ioc/security/sysmon/apt-29-phishing-campaigns",
]
# To exclude any rule for deployment, add rule paths from content directory.
exclude_rules = [
"ioc/application/powershell/suspicious-powershell-zipping-activity",
]
To add any custom detection rules to your environment refer to Deploying custom rules.
ML Behavior Rules
File Path
infrastructure-live/azure/.template/resource-groups/security-log-analytics/services/sentinel-rules/config.tpl.hclThere are currently 2 Machine Learning Behavior Analytic rules available for deployment (with their respective GUIDs in brackets) 1. Anomalous RDP Login Detections (737a2ce1-70a3-4968-9e90-3e6aca836abf)
- Anomalous SSH Login Detection (fa118b98-de46-4e94-87f9-8e6d5060b60b)
We utilize the rule’s GUID for deployment via terraform.
- Open
config.hcland under themachine_learning_behavior_rulesfield - Add in the array of rule GUIDs of suitable Sentinel Machine Learning Behavior Analytic Rules you would like to deploy.
inputs = { # Adds Sentinel Machine Learning Behavior Analytics Alert Rules. # We select these ML behaviour rules based on the gallery content's GUID. # Leaving the array empty or by not passing the machine_learning_behavior_rules array, no ML behavior rules will be deployed. machine_learning_behavior_rules = [ "737a2ce1-70a3-4968-9e90-3e6aca836abf", "fa118b98-de46-4e94-87f9-8e6d5060b60b" ]

Fusion Detection Rules
File Path
infrastructure-live/azure/.template/resource-groups/security-log-analytics/services/sentinel-rules/config.tpl.hclFusion rules are enabled via the detection rule Advanced multistage attack detection.
- Open
config.hcland under thefusion_rulefield - Set
fusion_rule = trueinputs = { # Setting the fusion_rule flag to true will deploy and enable Fusion via the Advanced multistage attack detection rule in Microsoft Sentinel. # Leaving this flag out or setting it to false would result in the rule not being deployed fusion_rule = true
If you would like to disable the rule, either set the flag to false or comment out the line.

For more information about Fusion rules, refer to Advanced multistage attack detection in Microsoft Sentinel
Workbooks
There are 2 types of workbooks: - Default workbooks are available for all customers.
- Custom workbooks are specific to a single environment.
There are 4 default workbooks that are deployed initially with an MDR deployment. 1. Ingestion Monitoring - Provides log ingestion information.
- SOC Report - Provides SOC metrics like Incident information, MTTA etc.
- Security Monitoring - Provides information on Critical entities, malicious traffic, detections etc.
- XDR Updates - Provides information on latest content added or updated.
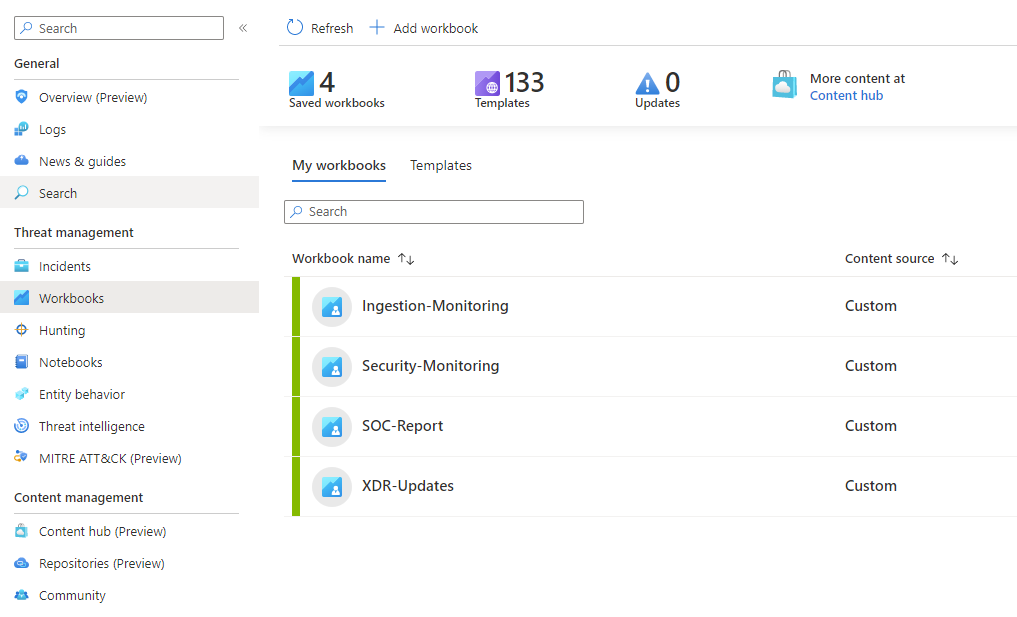
Default Workbooks
Default workbooks reside in infrastructure-modules/content/workbooks. To enable them, edit the file config.hcl (this is found in the below mentioned file path) and add the watchlist to the default_workbooks array.
default_workbooks = [
"Ingestion-Monitoring",
"Security-Monitoring",
"SOC-Report",
"XDR-Updates",
]Then run the update environment script.
Custom Workbooks
For additional Custom workbooks, place the JSON template of the workbook in the custom-workbooks directory in the file path as specified below. For more information on the format of the template, reference the sample default workbooks in infrastructure-modules/content/workbooks
Note: If you want Armor to build a custom playbook for you, rasie a service request on support portal.
To enable them, edit the file config.hcl (this is found in the below mentioned file path) and add the workbooks to the custom_workbooks array. For example:
custom_workbooks = [
"Sample-Workbook",
]Then run the update environment script.
File Path
infrastructure-live/azure/.template/resource-groups/security-log-analytics/services/sentinel-workbooks/Reference doc: Create workbooks
Playbooks
Incident notification playbook is deployed be default during initial deployment.
There are 2 types of playbooks: - Default Playbooks are available for all customers.
- Custom Playbooks are specific to a single environment.
Default Playbooks
Default playbooks reside in infrastructure-modules/content/playbooks. To enable them, edit the file config.hcl (this is found in the below mentioned file path) and add the playbook basename (without the extension, and without the directory path) to the default_playbooks array. For example:
default_playbooks = [
"Block-AADUser",
]Then run the update environment script.
Default playbooks need certain post-deployment prerequisite permissions in order to execute.
| Playbook | Auth | Permission |
|---|---|---|
| Block-AADUser | Sign In, Basic | User.Read.All, User.ReadWrite.All, Directory.Read.All, Directory.ReadWrite.All |
| Isolate-MDEMachine | Sign In | Machine.Isolate |
| Restrict-MDEAppExecution | Sign In | Machine.RestrictExecution |
| Restrict-MDEDomain | Basic | Ti.ReadWrite |
| Restrict-MDEFileHash | Basic | Ti.ReadWrite |
| Restrict-MDEIpAddress | Basic | Ti.ReadWrite |
| Restrict-MDEUrl | Basic | Ti.ReadWrite |
| Run-MDEAntivirus | Sign In | Machine.Scan, Machine.Read.All, Machine.ReadWrite.All |
| Unisolate-MDEMachine | Sign In | Machine.Isolate |
For Basic Auth: 1. Open the Logic app corresponding to the Playbook.
- In steps performing HTTP calls, head to the Authentication section.
- Add the username and password.

- Save your changes.
For Sign In Auth: 1. Open the Logic app corresponding to the Playbook.
- In steps performing actions on MDE, click on
Change Connectionat the bottom.

Add newconnection and click onSign In.

- Save your changes.
Custom Playbooks
For additional Custom playbooks, pull out ARM template JSON file of your logic app from Azure portal and place it in the custom-playbooks directory (you may need to create this) in the below mentioned file path.
Note: If you want Armor to build a custom playbook for you, rasie a service request on support portal.
To enable them, edit the file config.hcl (this is found in the below mentioned file path) and add the playbook basename (without the extension, and without the directory path) to the custom_playbooks array. For example:
custom_playbooks = [
"a-custom-playbook"
]Then run the update environment script.
File Path
infrastructure-live/azure/.template/resource-groups/security-log-analytics/services/sentinel-playbooks/Reference doc: Using Playbooks in Sentinel
Watchlist
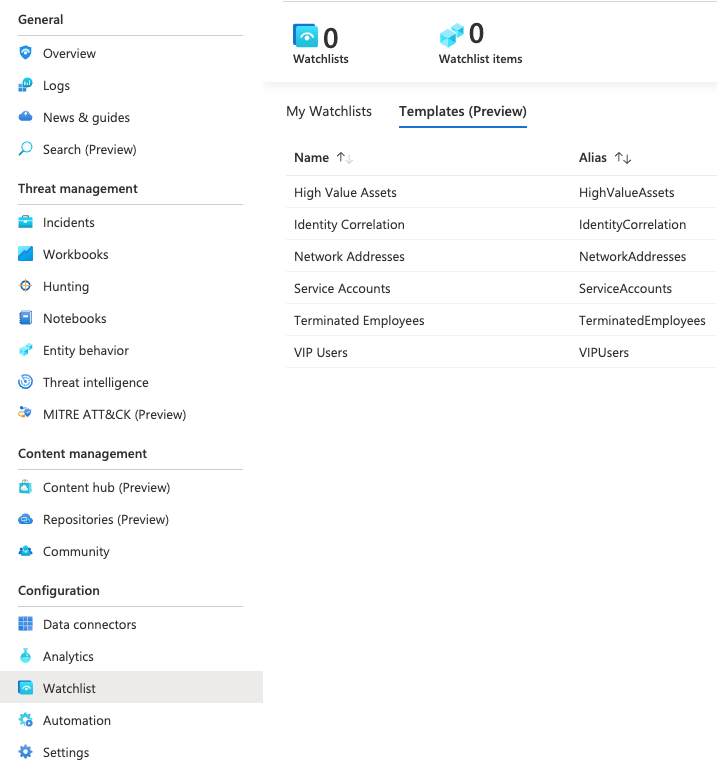
There are 2 types of watchlists: - Default watchlists are available for all customers.
- Custom watchlists are specific to a single environment.
Default Watchlists
Default watchlists reside in infrastructure-modules/content/watchlist. To enable them, edit the file config.hcl (this is found in the below mentioned file path) and add the watchlist to the default_playbooks array. You may choose the watchlist’s name and description, but you must obtain the watchlist_item_search_key and watchlist_item_properties_file from the respective csv in infrastructure-modules/content/watchlist. For example:
default_watchlists = [
{
watchlist_name = "SecurityIdCorrelation"
watchlist_description = "The Identity Correlation watchlist lists related user accounts that belong to the same person."
watchlist_item_search_key = "Email"
watchlist_item_properties_file = "SecurityIdentityCorrelation.csv"
},
]Then run the update environment script.
Custom Watchlists
For additional Custom watchlists, place the source csv in the watchlist-item-properties-files directory in the file path as specified below. Ensure that the csv has headers, at least one row of data and that the watchlist_item_search_key matches a column in the csv file.
Note: If you want Armor to build a custom playbook for you, rasie a service request on support portal.
To enable them, edit the file config.hcl (this is found in the below mentioned file path) and add the watchlist to the custom_watchlists array. For example:
custom_watchlists = [
{
watchlist_name = "SecurityIdCorrelation"
watchlist_description = "The Identity Correlation watchlist lists related user accounts that belong to the same person."
watchlist_item_search_key = "Email"
watchlist_item_properties_file = "SecurityIdentityCorrelation.csv"
},
]Then run the update environment script.
File Path
infrastructure-live/azure/.template/resource-groups/security-log-analytics/services/sentinel-watchlists/Reference doc: Create Watchlist
Threat Hunting
There are few default hunting queries readily available to be used inside infrastructure-modules/azure/content/rules/threat-hunting directory.
For any additional custom threat hunting queries to be deployed, refer to the sample hunting queries in the infrastructure-modules/azure/content/rules/threat-hunting directory. Follow the sample queries in the yaml format to construct your own custom hunting queries in the yaml format. Place the hunting query’s yaml file in the custom-threat-hunting-queries directory in the below mentioned file path and run the update environment script. We will utilise the attributes ‘name’, ‘query’, ‘techniques’ and ‘tactics’.
To enable a default hunting query, edit the file config.hcl (this is found in the below mentioned file path) and add the path to the yaml file to the default_threat_hunting_queries array. For default hunting queries, the path is referenced relative to infrastructure-modules/azure/content/rules/threat-hunting. For example:
default_threat_hunting_queries = [
"linux/account-manipulation-ssh-authorized-keys-on-linux-via-file-creation.yaml",
"firewall/port-scan.yaml",
"application/powershell/dismount-virtual-hard-drive-file-via-powershell.yaml",
]Note : Avoid using special characters in the name of the hunting query (with the exception of round brackets/parenthesis) as it may cause errors in the deployment.
To enable a custom hunting query, edit the file config.hcl (this is found in the below mentioned file path) and add the yaml file to the custom_threat_hunting_queries array. For custom hunting queries, the path is referenced relative to the custom-threat-hunting-queries directory. For example:
custom_threat_hunting_queries = [
"custom-hunting-query.yaml",
]For more information, refer to the comments in config.hcl.
File Path
infrastructure-live/azure/.template/resource-groups/security-log-analytics/services/sentinel-threat-hunting/Reference doc: Threat Hunting
Automation Rules
Default automation rules will be available to be used inside the infrastructure-modules/azure/content/automation-rules directory.

For any additional custom automation rules to be deployed, refer to the sample automation rules in the infrastructure-modules/azure/content/automation-rules directory. Construct your own custom automation rules in the JSON format. Place the JSON file in the custom-automation-rules directory in the below mentioned file path and run the update environment script.
To enable a default automation rule, edit the file config.hcl (this is found in the below mentioned file path) and add the path to the JSON file to the default_automation_rules array. For default automation rules, the path is referenced relative to infrastructure-modules/azure/content/automation-rules. For example:
default_automation_rules = [
"Default-Automation-Rule",
]To enable a custom automation rule, edit the file config.hcl (this is found in the below mentioned file path) and add the JSON file to the custom_automation_rules array. For custom automation rules, the path is referenced relative to the custom-automation-rules directory. For example:
custom_automation_rules = [
"Custom-Automation-Rule",
]Note: If you want Armor to build a custom playbook for you, rasie a service request on support portal.
For more information, refer to the comments in config.hcl. To design the automation rules, please refer to the terraform documentation to see the supported options and features: Automation rules - azurerm_sentinel_automation_rule
File Path
infrastructure-live/azure/.template/resource-groups/security-log-analytics/services/sentinel-automation-rule/Reference doc: Create automation rules
