Using the Datalake for EDR
Understanding the Datalake
The Armor data lake is a centralized repository for storing Armor collected data. With regards to EDR, the data lake contains data for incidents in every environment, including endpoints. This can be a lot of data so narrowing down the scope of information is critical to making sense of it all.
Accessing the Datalake
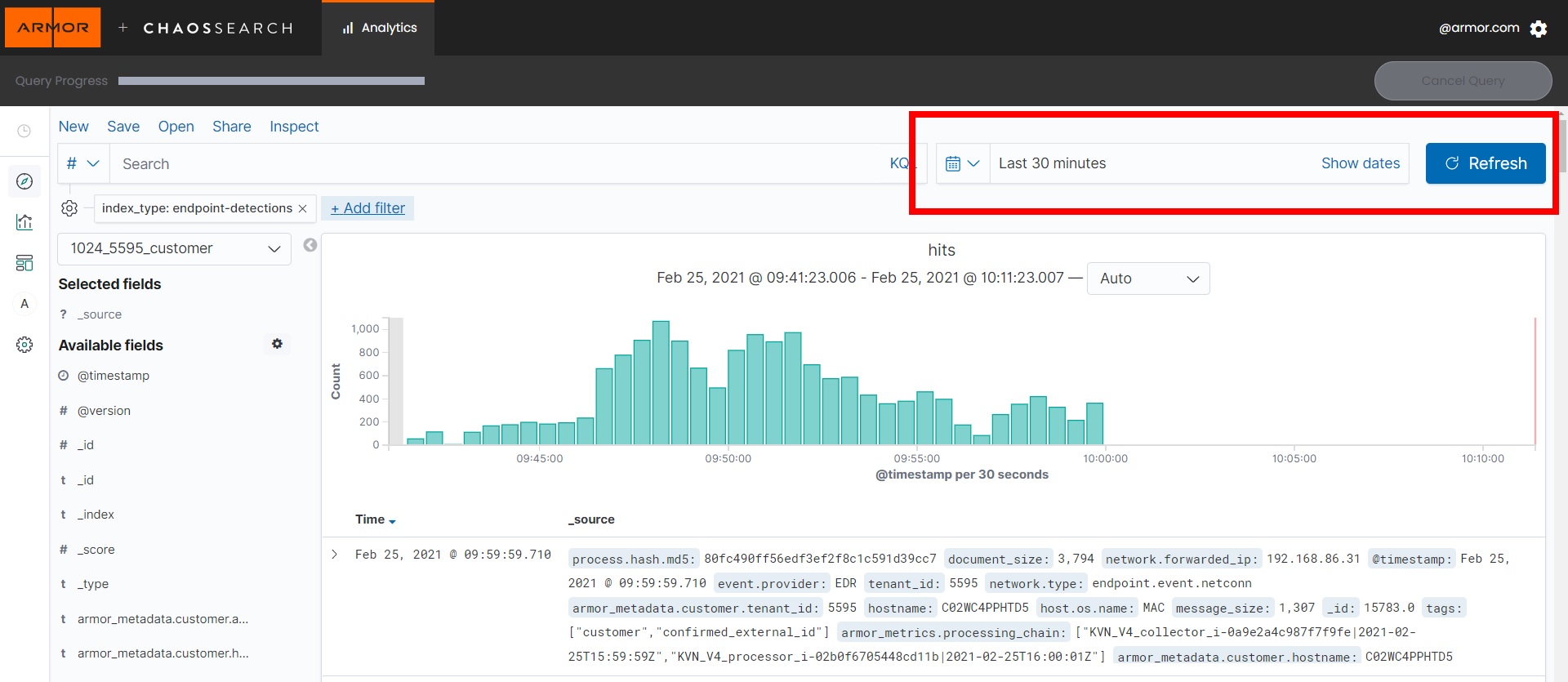
In Nexus, hover over Threat Management
 on the left-side nav.
on the left-side nav.Click Log Search.
Then click Log Search tab on the top of the page.
Wait for the SSO.
Note: If you are using the Armor Management Portal (AMP), you can follow the same steps. Find Log Search under Armor Services in the Security section of the left-nav
Create a filter by doing the following:
Click on Add filter.
In Field select
index.type.Select
isfor Operator.In the Value field, type
endpoint-detections.Click Save.
Now set the date range to encompass the incident date or dates to show and click Refresh.
Data Presentation
Data consists of documents stored in the datalake. Each document contains all the data related to that particular rule and resource. Below are examples of the table and JSON views:
Helpful Fields for Searching the Datalake
Field | Filter By |
|---|---|
event.type | This is one of four ECS Categorization Fields, and indicates the third level in the ECS category hierarchy. |
host.hostname | Hostname of the host. |
host.os.name | OS fields contain information about the operating system. |
Adding a Filter
To add additional filters, click on the Add Filter Button.
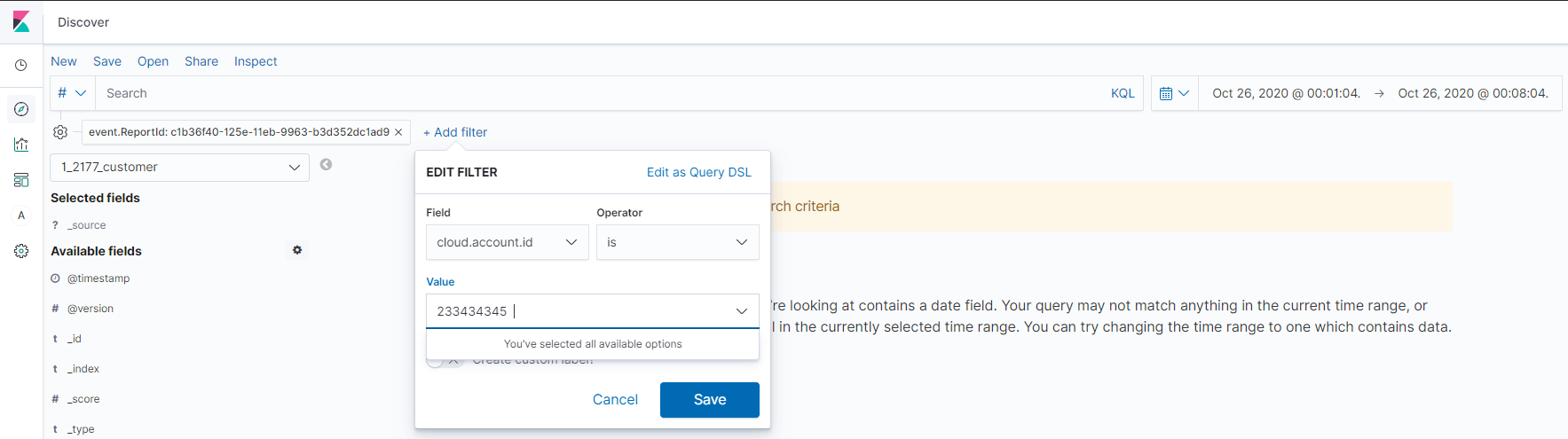
Then set the field to one of the helpful fields above, select the operator, put in the value and hit save.
