Create an Agent Based Log Source - MSSQL
Assumptions
Running SQL Server 2016 or higher
The Armor Agent is already installed and configured for Windows Logs
Working knowledge of SQL server administration
The user has access to the Security Log
User has privileged access to enable security logging
Procedure
Following the Microsoft documentation, linked below, modify permissions to write SQL Server Audits to the Security log
Create a Server audit object, using the following steps
In the left hand panel, right click on security, and select new → audit
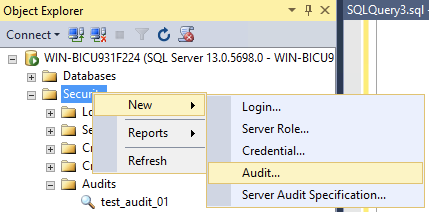
Set the audit name to be something identifiable for you
Change the audit destination to be
Security LogLeave the rest of the options as the default, and then press ok
Right click on the new audit object and select
Enable Audit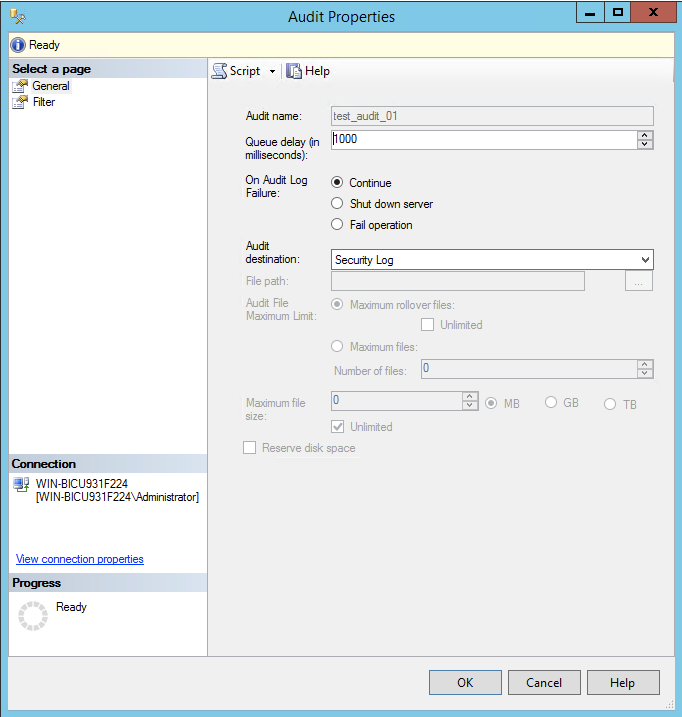
Create a new Server audit specifications object using the following steps
In the left hand panel, right click on security, and select new → Server audit specification
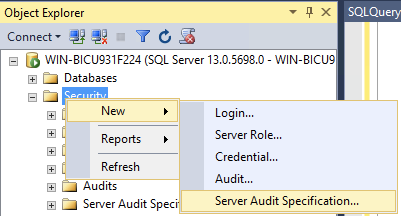
Name the audit specification object something identifiable for you
In the
Auditfield, select the audit that you just createdIn the
Audit Action Typefield, select the following options, each on a different lineAUDIT_CHANGE_GROUPFAILED_LOGIN_GROUPSERVER_STATE_CHANGE_GROUPSERVER_OPERATION_GROUP
Press OK to save the Server audit specifications
Right click on the new Audit specification object and select
Enable server audit specification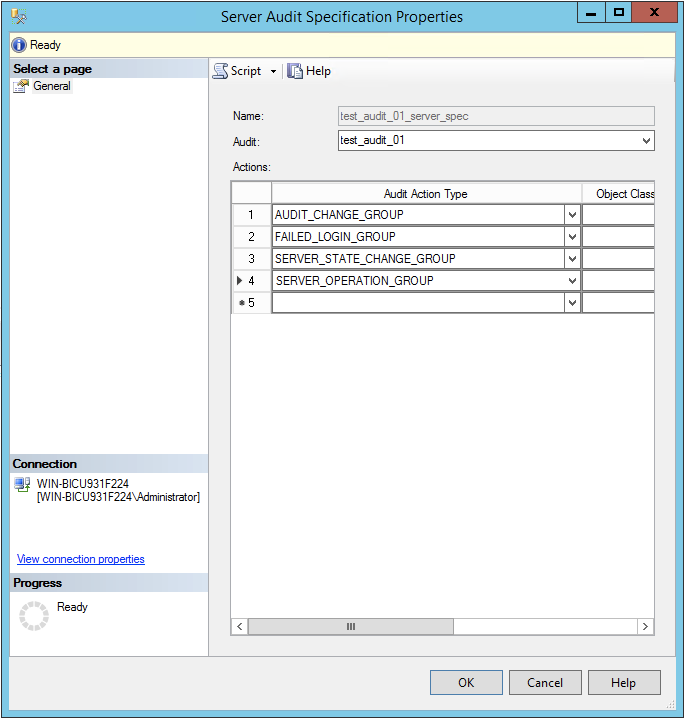
For each database that will be monitored, create a new Database audit specification object, and apply the settings to it as follows
In the left hand panel, navigate to the database that will be monitored, right click security, and select new → Database audit specification
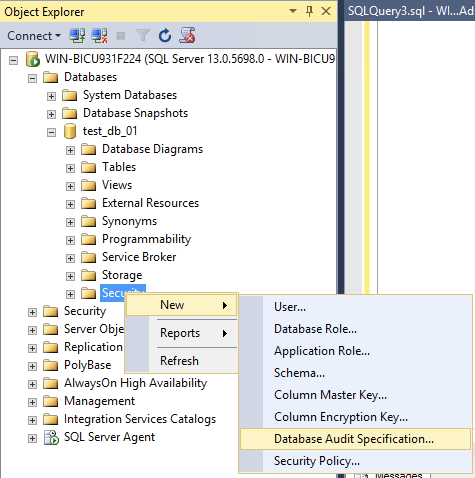
Name the audit specification object something identifiable for you
In the
Auditfield, select the audit that was just createdIn the
Audit Action Typefield, select the following options, each on a different lineDATABASE_OBJECT_ACCESS_GROUPDATABASE_ROLE_MEMBER_CHANGE_GROUPDATABASE_LOGOUT_GROUPSUCCESSFUL_DATABASE_AUTHENTICATION_GROUPDATABASE_PERMISSION_CHANGE_GROUPDATABASE_PRINCIPLE_CHANGE_GROUPDATABASE_OBJECT_CHANGE_GROUPSCHEMA_OBJECT_CHANGE_GROUP
Press OK to save the database audit specification
Right click on the new audit specification object and select
Enable database audit specificaiton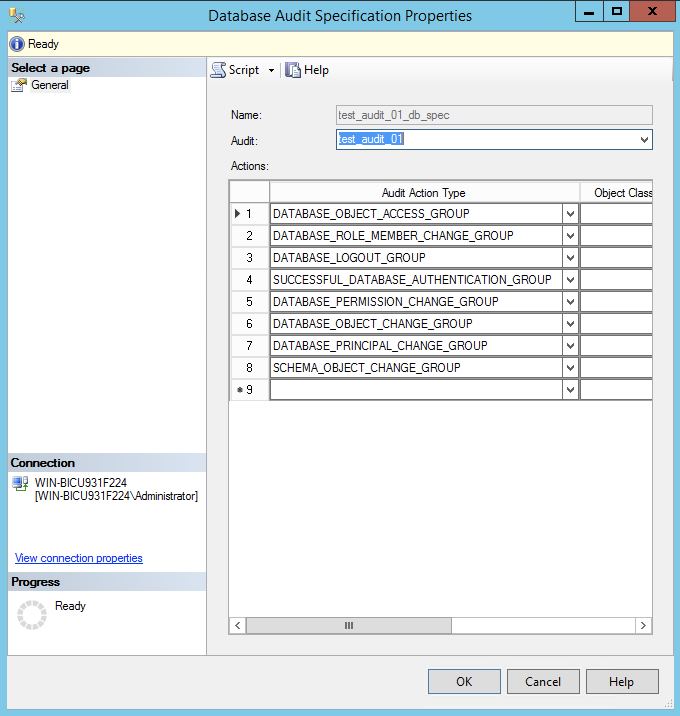
MSSQL Rules
Rule | Definition |
|---|---|
Classification | Classify SQL Database devices for ease of identification |
Audit Changed | Alerts if the SQL audit object is changed or disabled |
SQL Server Stopped | Alerts if the SQL Server stops on the host |
User Granted Access to Database | Alerts if a new user is granted access to a database |
User Removed Access to Database | Alerts if a user is removed from a database |
Truncate or Drop | Alerts if a truncate or drop action is performed |
SQL Server Failed Login Attempt | Alerts if there is a failed authentication attempt to a database |
