Log Management Overview
How Do I Get Started?
Follow these steps to start collecting logs:
Step 1
Sign up for a free Armor demo.
Step 2
Configure your Log Source.
Product Overview
Armor Log and Data Management provides security, operational visibility, and brings organizations into compliance with cybersecurity regulations. Armor Anywhere is used to collect logs from the security capabilities within the agent as well as from cloud native and third-party log sources. Logs ingested and analyzed by Armor are made visible through Nexus and the legacy Armor Management Portal (AMP), Armor's Security Incident Connector, or via API. Log and Data Management allows Armor to extend its reach into an organization's broader security and IT footprint, beyond just workload protection and works by allowing Armor to take in logs from three source groupings:
Armor Agent
Native System Logs
Web Logs
MSSQL
Sysmon
Amazon AWS
Microsoft Azure
Third Party Sources
Virtualized appliances
Network devices, firewalls
Endpoint detection and response tools
Switches
Features
Security Analytics
Ingest logs from more sources and providing deeper context into customer environments
Armor ingests logs from any cloud-hosted network, including agent sources such as Apache, third-party log relay sources such as Check Point or Cisco, and CSP security feeds such as AWS CloudTrail and GuardDuty. Armor provides added analytics tools including a search and analytics engine. Nexus and Armor Management Portal (AMP) users can now search time and date ranges for specific IOCs to discover patterns or establish context behind incidents.
With enhanced log and data management capabilities, security professionals can dig deeper into what is occurring in their environments. Operators can identify their own IOC hashes and determine their threat response or follow up with recommendations from the Security Operations Center.
Visualization and Dashboards
Build customer dashboards within Nexus
Armor provides advanced log search and data visualization capabilities through Nexus and the legacy Armor Management Portal (AMP). The benefits of Armor's log and data management add-on include:
Enhanced security posture through the analysis and correlation of log information with other Armor telemetry sources.
Greater context to aid in more effective detection, alerting and response.
Ability to meet compliance mandates through the storing of log data for up to 13 months.
Values of data can help security teams visualize what is occurring in each environment. Users can then process that data to develop reports and graphs, making it easier to share with others. Once data is gathered, users can then take advantage of the virtualization and reporting capabilities with just a few clicks. Visualize log alerts and incident information within any environment. Armor Log and Data Management correlates events to minimize "noise" and increase the fidelity of detection and alerting. By examining logs in real-time, intrusions can be detected as soon as they happen. Visibility into logs provides application-specific data for incident investigation. Using logs, organizations can pinpoint the how, why, and when of an attack.
Compliance Features
Audit ready compliance
Meet PCI DSS, HIPAA/HITRUST, GDPR and other compliance requirements related to the collection, analysis, and storage of log information. Log and Data Management gives users better ability to meet compliance mandates through the storing of log data for up to 13 months.
Pricing
Pricing is based on each GB of log data consumed. Customer may purchase customized configuration, custom log sources, and log exports at an additional cost. To do so, Customer must contact its Armor Account Manager to define the scope of these additional services and to create a statement of work for the customizations. Pricing will be defined in the statement of work.
Use Cases
The following use cases will help you get started collecting and analyzing logs from a variety of sources.
Log Collection Through the Armor Agent
Correlation and Threat Intelligence
Armor collects event data from Armor Anywhere's integrated security capabilities such as from the intrusion detection/prevention system, file integrity monitoring, vulnerability scanning and malware protection. The logs are stored and can be correlated and analyzed against threat intelligence feeds from Armor and other third parties.
Network Flow Sources
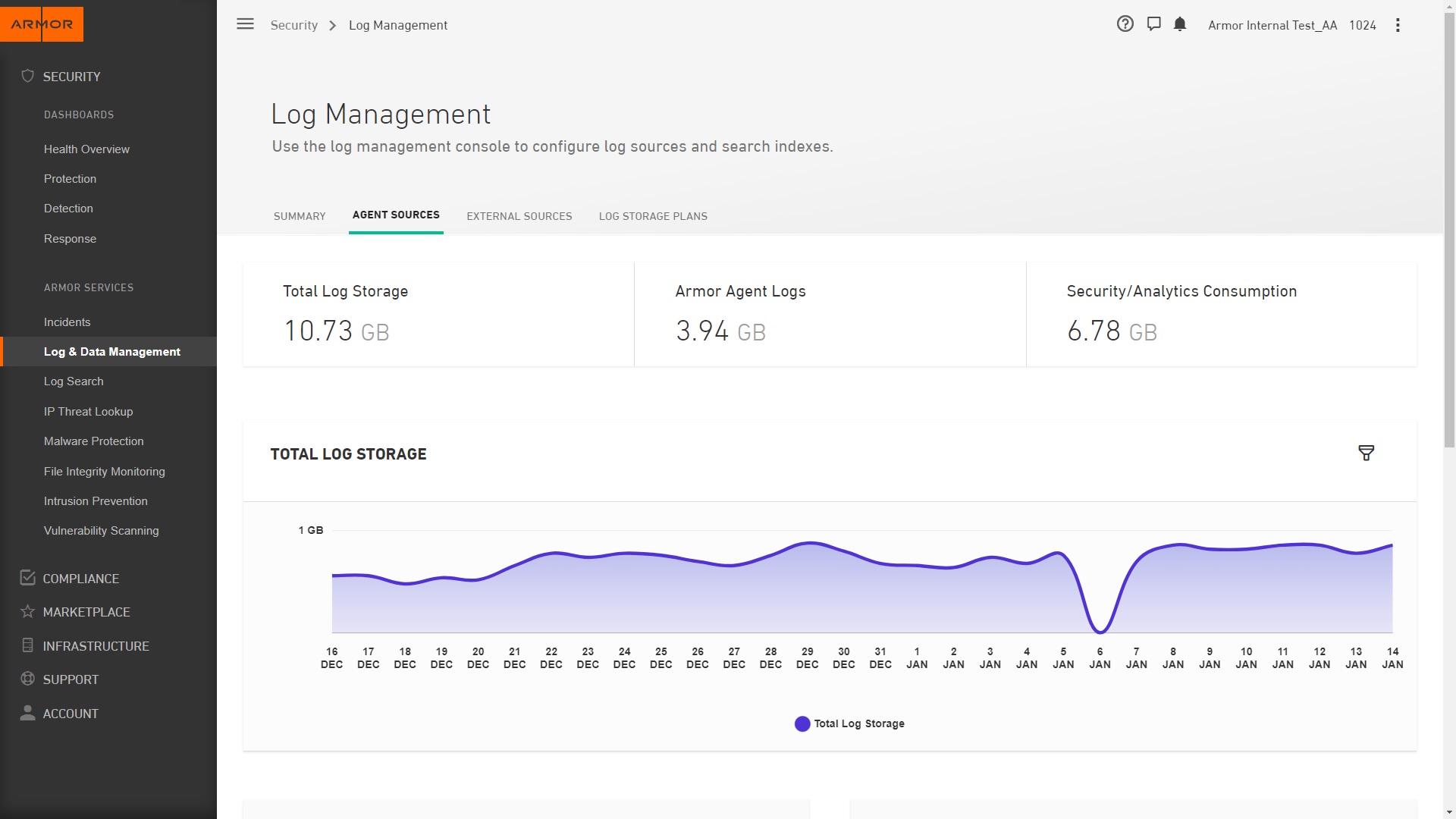
View Agent and Cloud Source Status
Armor Anywhere is used to collect logs from the security capabilities within the agent as well as from cloud native and third-party log sources. Logs ingested and analyzed by Armor are made visible through Nexus and the legacy Armor Management Portal (AMP), Armor's Security Incident Connector, or via API. Armor Log Management can be configured to collect logs from Amazon AWS and Microsoft Azure within Nexus or AMP.
Third Party Sources through Armor Log Relay
Collecting Syslog Based Logs
Also known as remote log collection, Syslog based logs collect different device logs from machines like switches, firewalls, and routers to a central location for review. To send these remote logs, you must obtain Log Relay and then create and configure your remote Log Relay device.
Related Documentation
To learn how to collect and send additional log types to Nexus and AMP, see Introduction to Log Relay.
