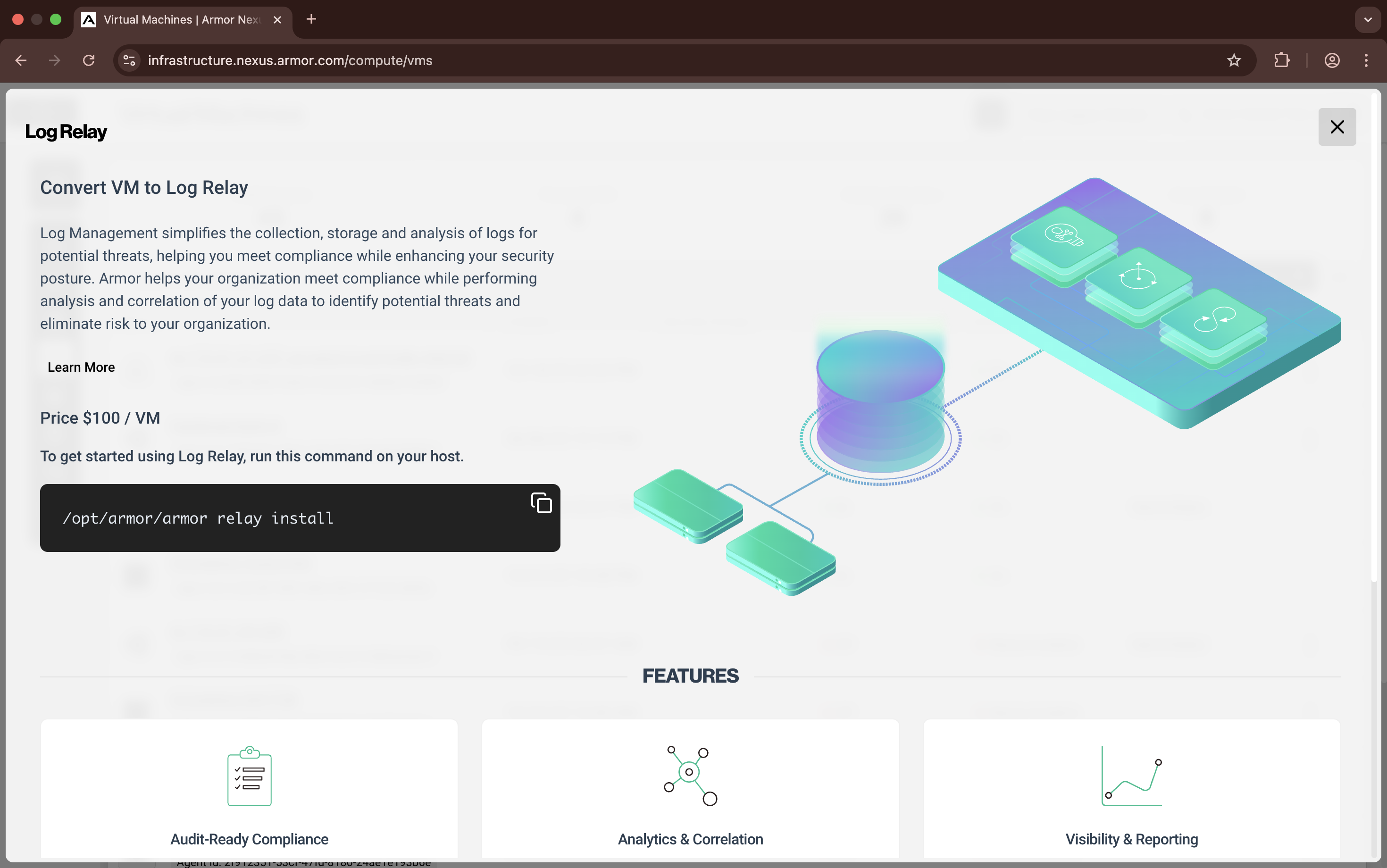
Obtain Log Relay for Remote Log Collection
Topics Discussed
You can use this document to learn about the specific, high-level steps needed to obtain Log Relay, and send additional log types to Armor's Security Information & Event Management (SIEM).
Before you begin:
For Armor Enterprise Cloud users, you must already have a virtual machine in your account
To learn how to create a virtual machine, see Virtual Machines.
For Armor Anywhere users, you must already have downloaded and installed the Armor Agent.
To learn how to download the Armor Agent, see Install the Armor Anywhere Agent - Linux.
For introductory information on Log Relay, see Introduction to Log Relay.
Review Requirements
Requirement Type | Product Compatibility | Description | ||||||||||||||||||||
Supported Devices |
| Only Linux machines can be converted to Log Relays. Machines must be in an OK state to be converted. Supported Linux Distributions:
To learn more about the health status of a virtual machine, see Health Overview Dashboard. Log Relay will support receiving logs from devices such as WAFs or next-gen firewalls. The Armor Agent is not needed on devices to pass logs through a relay. | ||||||||||||||||||||
Pricing Information |
| While log collection is available to all users, there is a cost associated with sending and storing logs. For pricing information, please contact your Account Manager. | ||||||||||||||||||||
Permissions |
| In order to use Log Relay, you must have the following permissions included in your account:
To learn more about permissions, see Roles and Permissions. | ||||||||||||||||||||
Log Retention Plan |
|
This plan:
For pricing information, please contact your Account Manager. Armor Anywhere agents that are converted to a log relay device will retain the default Log Management Essentials plan subscription. This plan collects and stores your logs for 30 days. | ||||||||||||||||||||
Firewall Rules |
| Armor Anywhere users must add the following generic firewall rules: Inbound:
Outbound:
The above-mentioned ports do not provide security analytics. To receive security analytics for logs from supported remote log devices, you must add additional firewall rules; these additional ports are described in the configuration documents listed in Create and Configure Remote Log Sources. For non-supported remote log sources, collected logs will not receive any security analytics. To learn more about firewall rules, see Requirements for Armor Anywhere. |
Obtain Log Relay
When you convert a virtual machine into a Log Relay device, your virtual machine / device will still contain the default Armor Agent components, such as FIM, Malware, Patching, etc.
After you have converted your virtual machine into a Log Relay device, see Create and Configure Remote Log Sources to learn how to create and configure a remote log source.
Troubleshooting
In general, if you are having issues adding Log Relay to a remote log device, consider that you need to update your permissions in Nexus.
To add the above-mentioned Nexus permissions to your account, see Roles and Permissions.