Create An Agent Based Log Source - Sysmon
You can use this document to collect Sysmon logs and send them to Armor's Log and Data Management platform.
Configure Your Sysmon Service
Configuring Sysmon services uses the Command Line Interface (CLI) feature. For more information, see Security Service CLI Commands.
The following arguments to install and uninstall Sysmon services.
The following arguments are possible parameters for the Logging CLI feature.
Installation of Sysmon
Install the sysmon service
C:\.armor\opt\armor.exe sysmon installAdd the event log, specific to Sysmon, to the Armor logging service.
C:\.armor\opt\armor.exe logging add-event-logs "Microsoft-Windows-Sysmon/Operational"Sync the logging config
C:\.armor\opt\armor.exe logging sync-event-logsRemoval of Sysmon
Remove the sysmon service
C:\.armor\opt\armor.exe sysmon uninstallRemove the event log from the logging service
C:\.armor\opt\armor.exe logging remove-event-logs "Microsoft-Windows-Sysmon/Operational"Sync the logging config
C:\.armor\opt\armor.exe logging sync-event-logsAccessing The Datalake
The Armor data lake is a centralized repository for storing Armor collected data that can be accessed through Nexus
Note: You can also access Chaos Search from the legacy Armor Management Portal (AMP). Navigate to Security -> Log Search and SSO into Chaos Search.
In Nexus, hover over Threat Management
 .
.Then click Log Search.
On the top of the page, click the tab labeled Log Search.
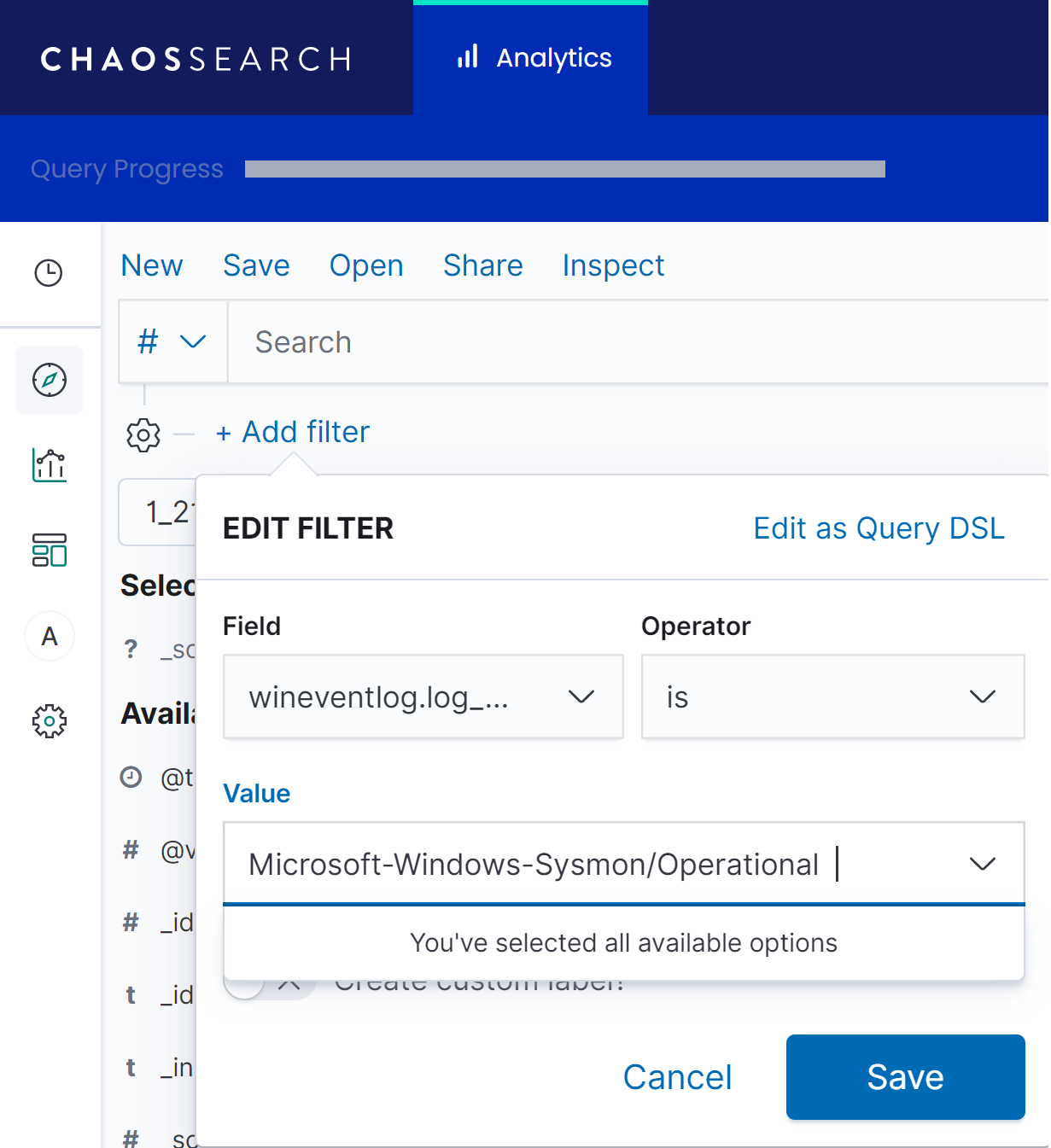
Create a filter by doing the following:
Click on Add filter.
In Field select wineventlog.log_name.
Select is for Operator.
Enter the value Microsoft-Windows-Sysmon/Operational into the Value field.
Click Save.
Now set the date range and click Refresh.
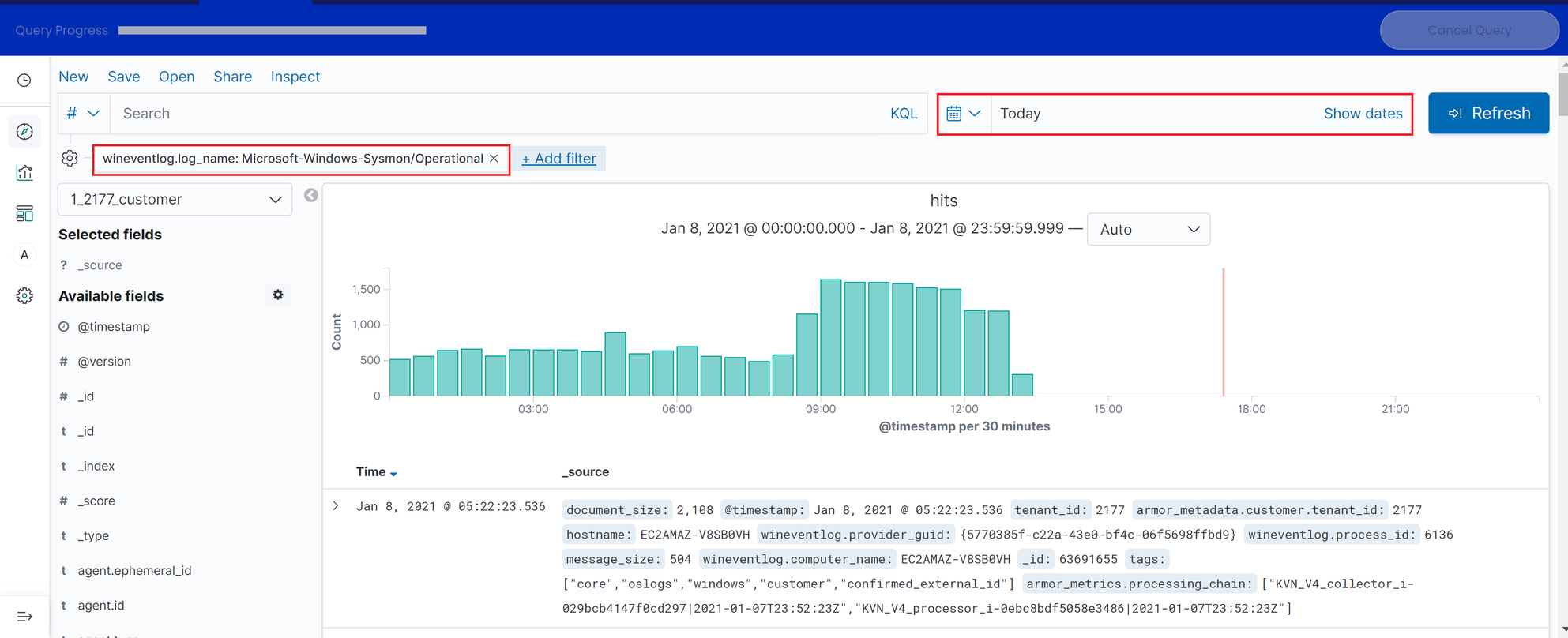
Data Presentation
Data consists of documents stored in the datalake. Each document contains all the data related to that particular rule and resource. Below are examples of the table and JSON views:
Helpful Fields For Searching The Datalake
FIELD | FILTER BY |
wineventlog.log_name | Microsoft-Windows-Sysmon/Operational |
wineventlog.task | the task name |
wineventlog.event_id | the event id eg : 1,2,3,4,5,6,7 |
wineventlog.source_name | Microsoft-Windows-Sysmon |
Adding A Filter
To add additional filters, click on the Add Filter Button.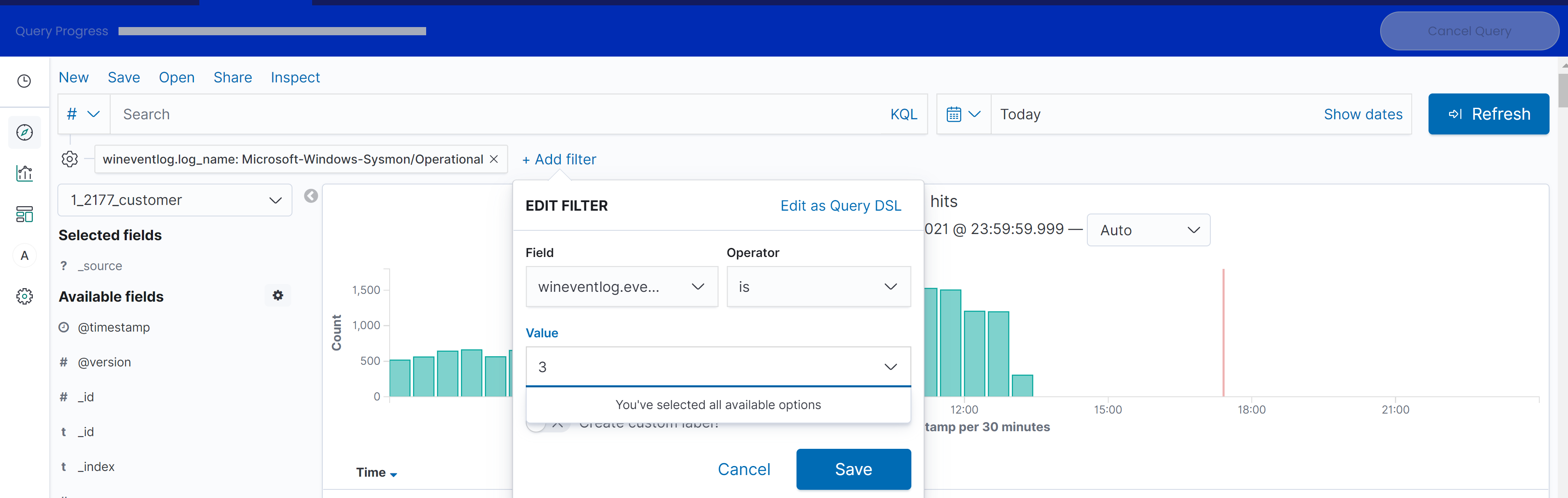
Then set the field to one of the helpful fields above, select the operator, put in the value and hit save. The data is now filtered on a specific log_name, event_id or other field selected.
Sysmon Rules
RULE | DESCRIPTION |
PsExec Process Observed on a Compromised Host | This rule triggers when a PsExec process has been detected on a host that has been identified as likely compromised. |
Administrative Share Accessed from a Compromised Host | Detects hosts that have been identified as likely compromised when they access Administrative shares. |
Network Share Accessed from a Compromised Host | Detects hosts that have been identified as likely compromised when they access networked shares. |
Powershell Process Observed on a Compromised Host | This rule triggers when a powershell process has been detected on a host that has been identified as likely compromised. |
Metasploit PSExec Module Usage | Detects the Metasploit implementation of the PSExec tool. |
Excessive System Tools Usage from a Single Host | Detects a large volume of several system tools being used from a single system. |
Excessive Network Share Access Failures from a Compromised Host | Detects hosts that have been identified as likely compromised when they access several networked shares in a short time period. |
Powershell Script Created by a Remote Management Service | Detects if any remoting service, such as wsmprovhost, psexesvc, or wmiprvse, creates a PowerShell script file. |
Unsigned Executable Loaded In Sensitive System Process | This rule is triggered on any attempt to load an unsigned executable file into sensitive system processes. |
Mimikatz IMP Hash Observed | Detects successful process creation matching the hash of 'Invoke Mimikatz PowerShell (IMP)'. |
Potential Keylogger Detected | This rule triggers when a potential keylogger tool is detected. |
Service Binary Path Update Followed by Remote Thread Creation | This rule triggers when a service binary path is updated and a remote thread is created by the same process. |
Executable Loaded from Temp Directory | This rule triggers when an executable is loaded from a temp directory. |
Remote Management Service Connected to lsass Pipe | Detects when a remote management service is connected to lsass pipe. |
Unusual Value Size in Windows Registry | This rule triggers when a value with an unusual size is set in Windows Registry. |
Service Binary Path Update Followed by User or Group Modification | This rule triggers when a service binary path is updated and a user or a group is modified on the same host. |
Suspicious Access to lsass Process From Unknown Call Trace | This rule triggers when a suspicious access to lsass is initiated from an unknown call trace. |
Fileless UAC Bypass using Windows Event Viewer | Detects when a registry event uses Windows Event Viewer has been detected. |
Process Launched from Unusual Directory | This rule triggers when a process is launched from an unusual directory. |
Excessive Use of SC Command | This rule triggers when the Service Control command is frequently used on a single host. |
Service Installed on a Compromised Host | This rule triggers when a service has been created on a host that has been identified as likely compromised. |
Thread Creation by a Process Launched from a Shared Folder | Detects when a process launched from a shared folder is creating a thread into another process. |
Group or Account Discovery | Detects when a command related to group or account discovery is detected. |
Unsigned Driver Loaded In Windows Kernel | This rule triggers when any unsigned driver is loaded in Kernel. |
UAC Bypass - Scheduled Task Configured to Run with Highest Privileges | Detects a potential User Account Control bypass when a scheduled task is configured to run with the highest privileges. |
Credential Dumping using SAM Registry Key | Detects when a resource is enumerating users sub-keys. |
Download via Encoded Command Initiated | This rule triggers when a download of a PowerShell script is initiated from cmd.exe or Powershell. |
Programming Environment Started with a Privileged Account | Detects when a programming environment has been started with a privileged account. |
Suspicious Access to lsass Process | This rule triggers when a process connects to lsass that does not normally. |
Process Launched by an Unusual Process | This rule triggers when a process that is not supposed to have child launches a process. |
Excessive Administrative Share Access Failures from the Same Host | Detects repeated failures to access administrative shares from the same host. |
Thread Creation by a Process Launched from a Temp Directory | This rule triggers when a thread is created by a process launched from a temp directory. |
Detected an Unquoted Service Binary Path with Spaces | Detects if an unquoted service binary path contains spaces. A file path that is not enclosed within quotation marks and contains spaces in the path can be leveraged. |
Service Binary Path Update Followed by Network Connection | Detects if a process attempts to configure or add a service and detects if the same process creates an outbound connection. |
PsExec Process Masquerading | This rule triggers when PsExec IMP Hash is detected for another process name. |
Process Launched from a Temp Directory | This rule triggers when a process is launched from a temp directory. Temporary directories are common staging locations for malware execution or data exfiltration. |
Unusual Parent for a System Process | This rule triggers when an unusual parent is found for a system process. |
Thread Creation into lsass Process | This rule triggers when a thread is created into lsass process. |
Fileless UAC Bypass using sdclt | This rule triggers when a UAC bypass using sdclt has been detected. |
Unsigned Executable Loaded in lsass | This rule triggers when an unsigned driver is loaded in lsass. |
Rundll32 with qwerty Argument Usage | This rule triggers when rundll32 is executed with qwerty argument, which could indicate the presence of a Ransomware (type Locky). |
Service Configured to Use a Pipe | This rule triggers when a service is configured to use a pipe. |
Remote Process Execution on Multiple Hosts | This rule triggers when remote management service are creating process on multiple hosts. |
Service Configured to Use Powershell | This rule triggers when a service is configured to use Powershell. |
Scheduled Task Created on Multiple Hosts | This rule triggers when a scheduled task has been created on mulitple hosts. |
Service Binary Located in a Shared Folder | This rule triggers when a service binary is located in a shared folder. |
Process Launched from a Shared Folder | This rule triggers when a process is launched from a shared folder. |
Fileless UAC Bypass using Fodhelper | This rule triggers when a UAC bypass using Fodhelper has been detected. |
Shadow Copies Deletion | This rule triggers when deletion of shadow copies is detected. |
Potential Credential Dumping Tool Detected | This rule triggers when a potential credential dumping tool is detected. |
Pipe Created Followed by Service Binary Path Update | This rule triggers when a pipe is created and the service binary path is updated to connect to it. |
Scheduled Task Created on a Compromised Host | This rule triggers when a scheduled task has been created on a compromised host. |
Lsass Process Connected to a Pipe | This rule triggers when an lsass process is being connected to a pipe. |
Thread Creation into a System Process | This rule triggers when a process is creating a thread into a system process. |
Malicious Service Installed | This rule triggers when a service categorized as malicious has been installed. |
Hidden Network Share Added | This rule triggers when a hidden Network Share has been added. |
Thread Creation into a Process Different from the Initial One | This rule triggers when a process is creating a thread into another process. |
Network Share Added to a Compromised Host | This rule triggers when a network share has been added to a compromised host. |
System Process Launched from Unusual Directory | This rule triggers when a system process is launched from an unusual directory. |
Encoded Command Malicious Usage in a Programming Environment | This rule triggers when an encoded command is used in a programming environment type cmd or Powershell. |
Troubleshooting
Make sure that winlogbeat is configured for sysmon.
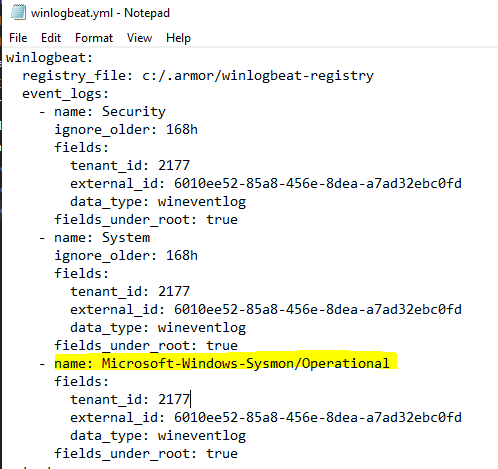
Make sure you have synched up the logs.
CODEC:\.armor\opt\armor.exe logging sync-event-logs
