Create a Remote Log Source - Imperva Incapsula
Topics Discussed
You can use this document to send Imperva Incapsula logs to Armor's Security Information & Event Management (SIEM).
Pre-deployment Considerations
To create a remote Log Relay, you must already have:
A Log Relay server on your account
To learn how to add Log Relay to your account, see Obtain Log Relay for Remote Log Collection
Configured the system clock
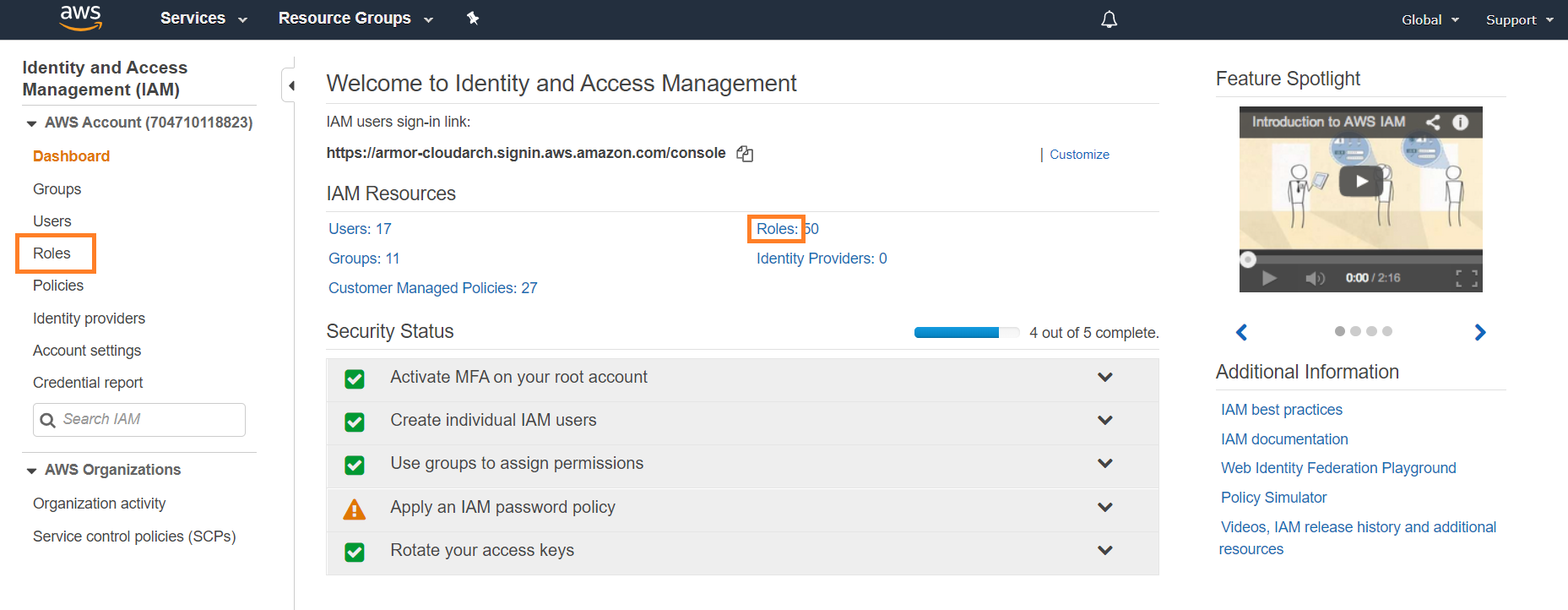
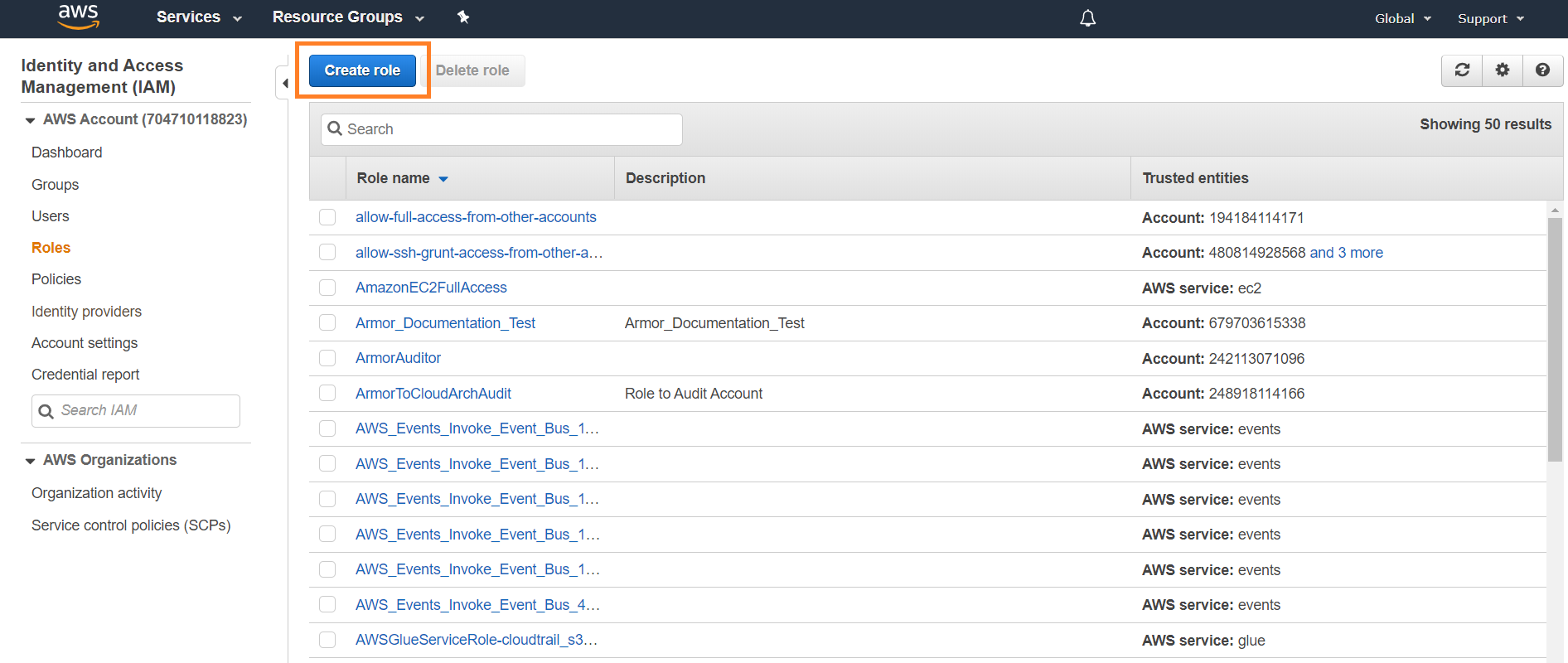
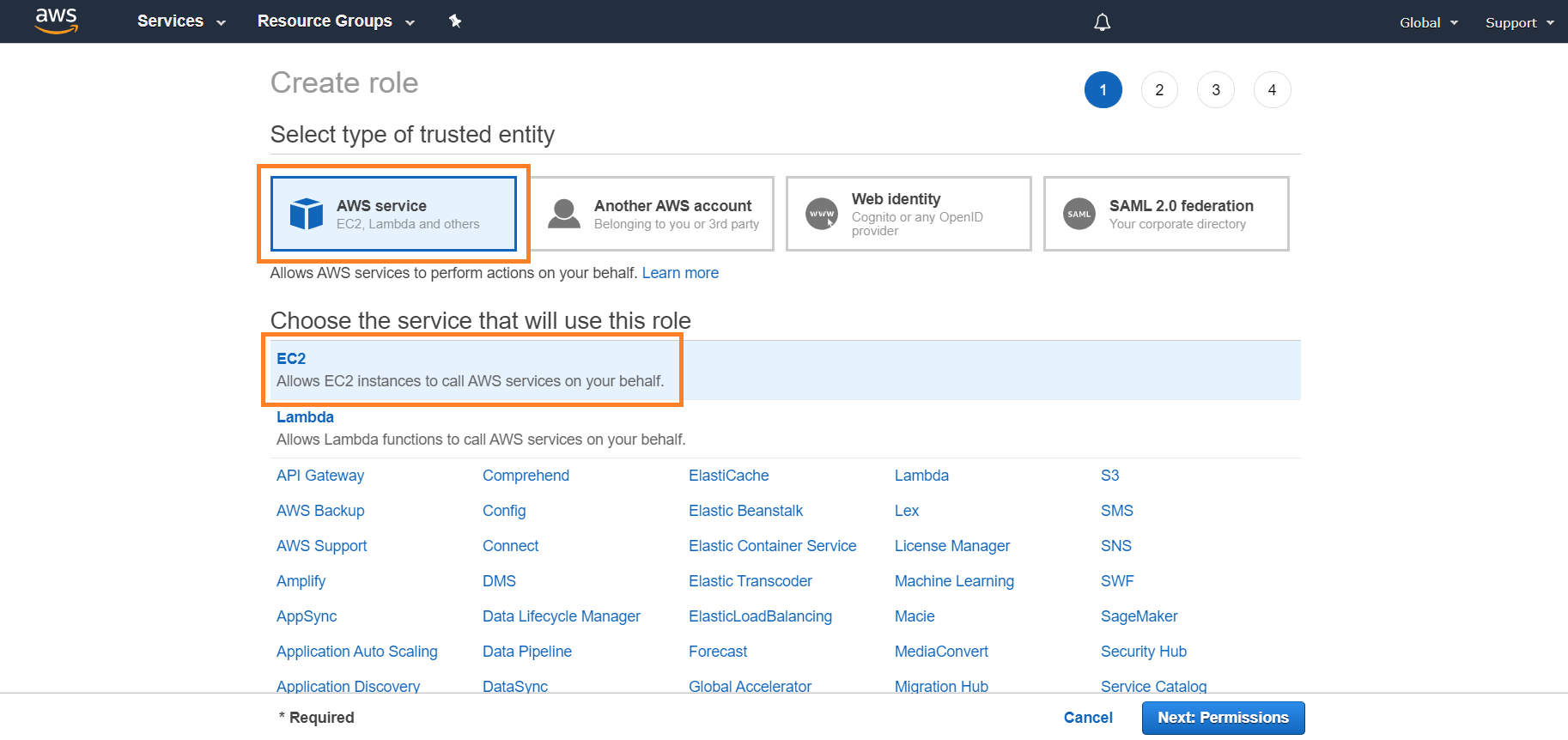
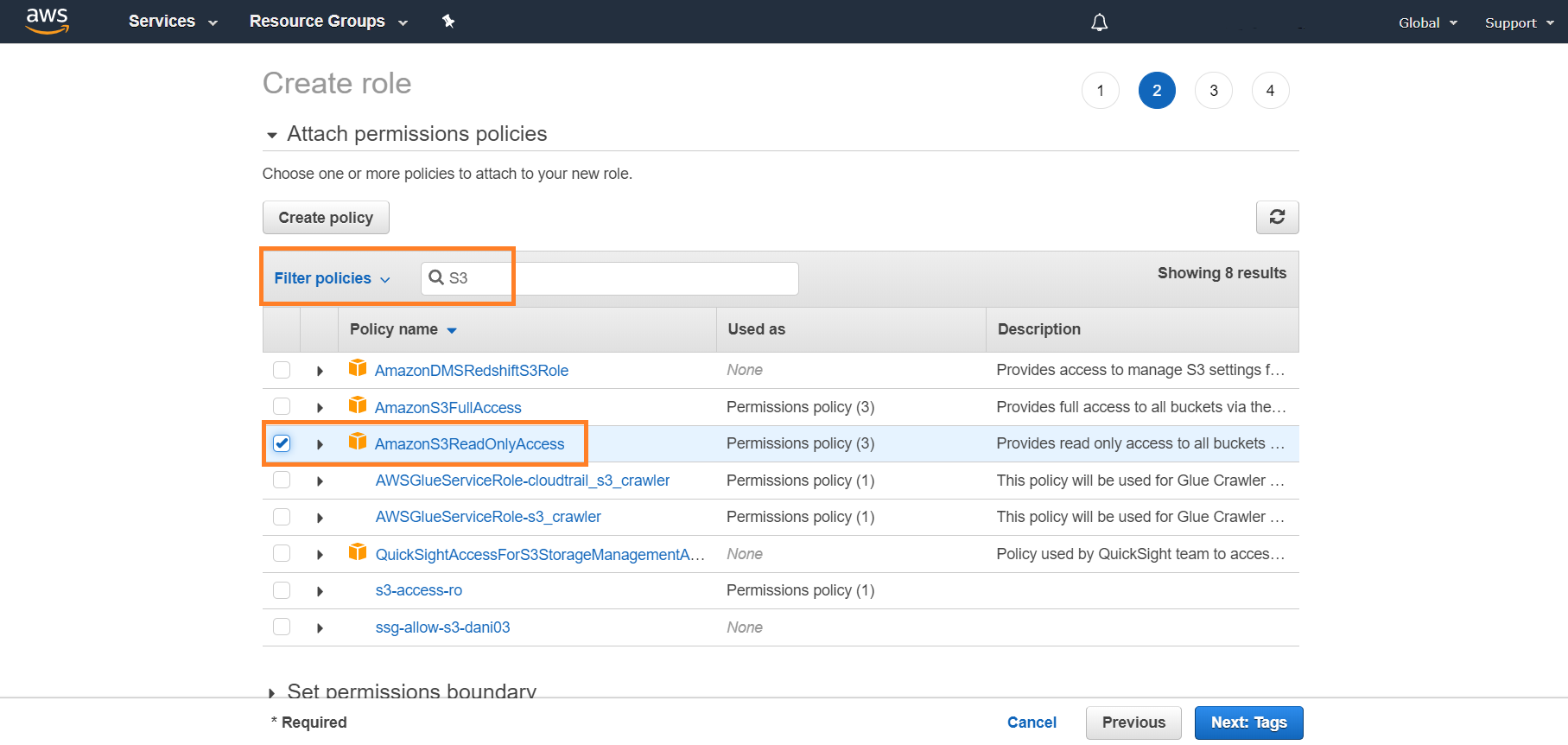
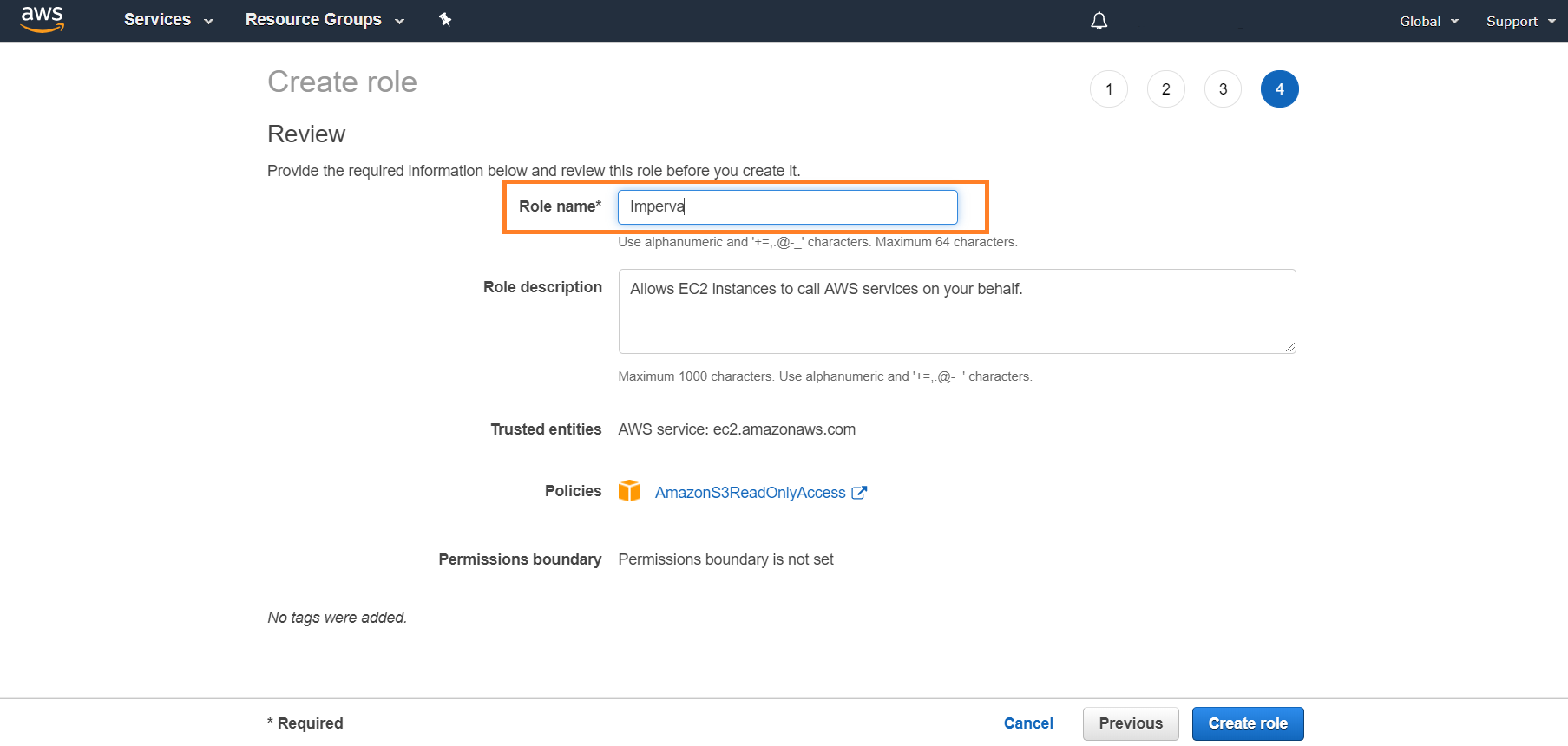
Configure the IAM Role
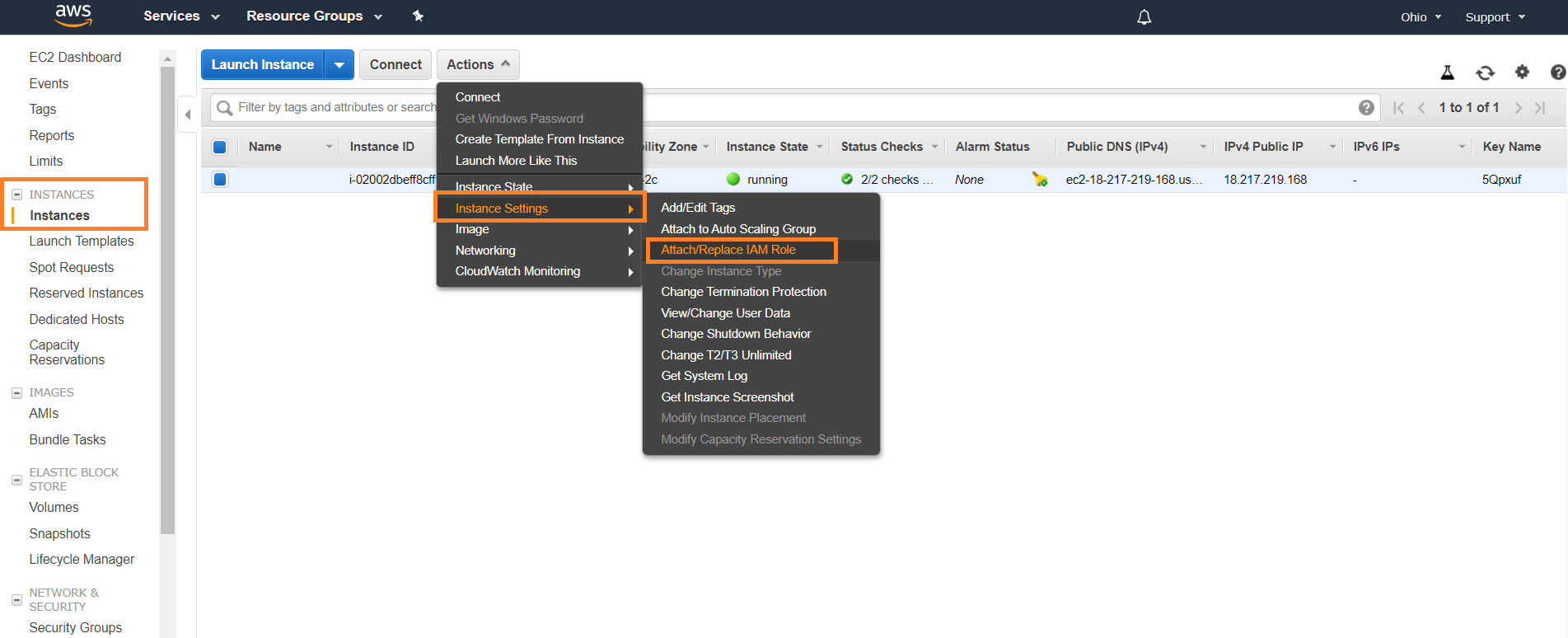
Assign a Role to the EC2 Instance
In the AWS console, go to the EC2 service.
Click Instances to find the EC2 instance that is the log relay, then click the box next to the instance.
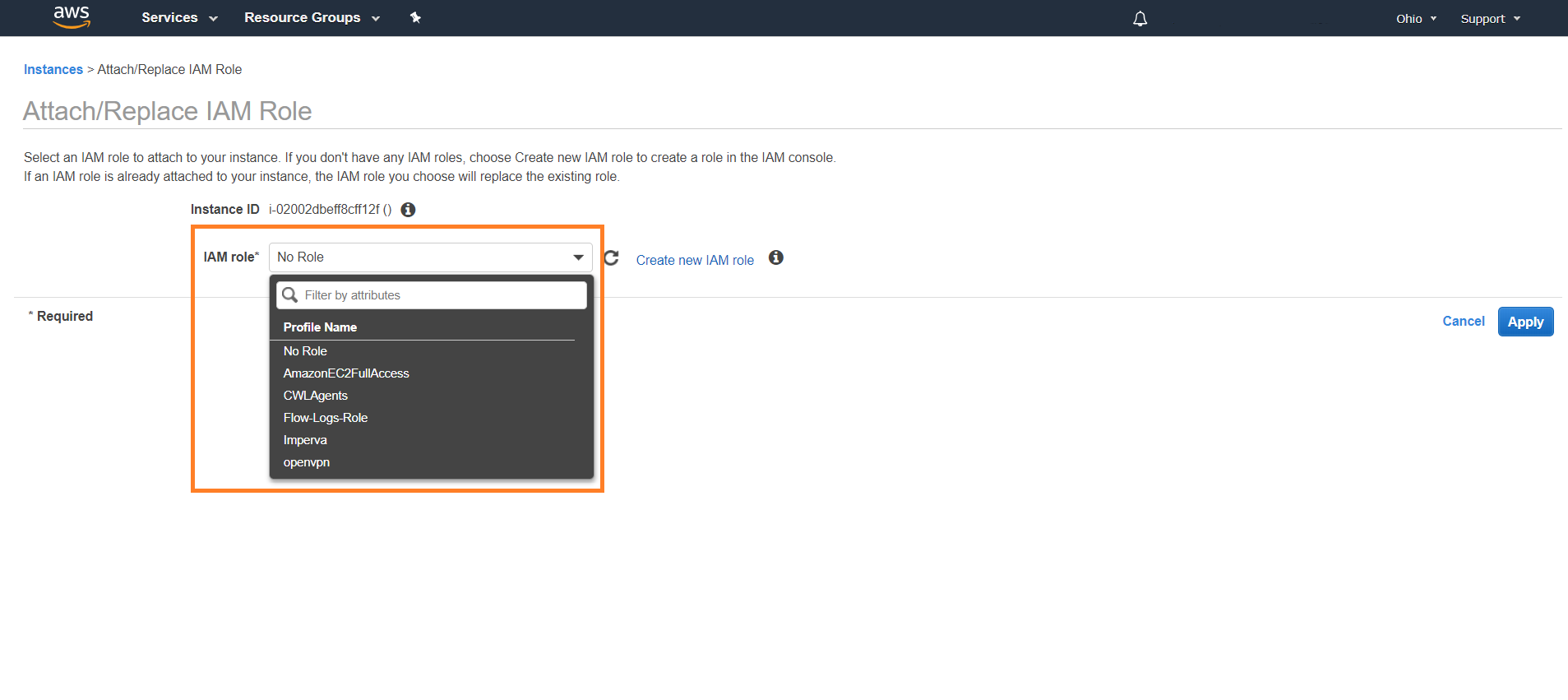
Select Actions > Instance Settings > Attach/Replace IAM Role.
In IAM role, select the role created.
Click Apply.
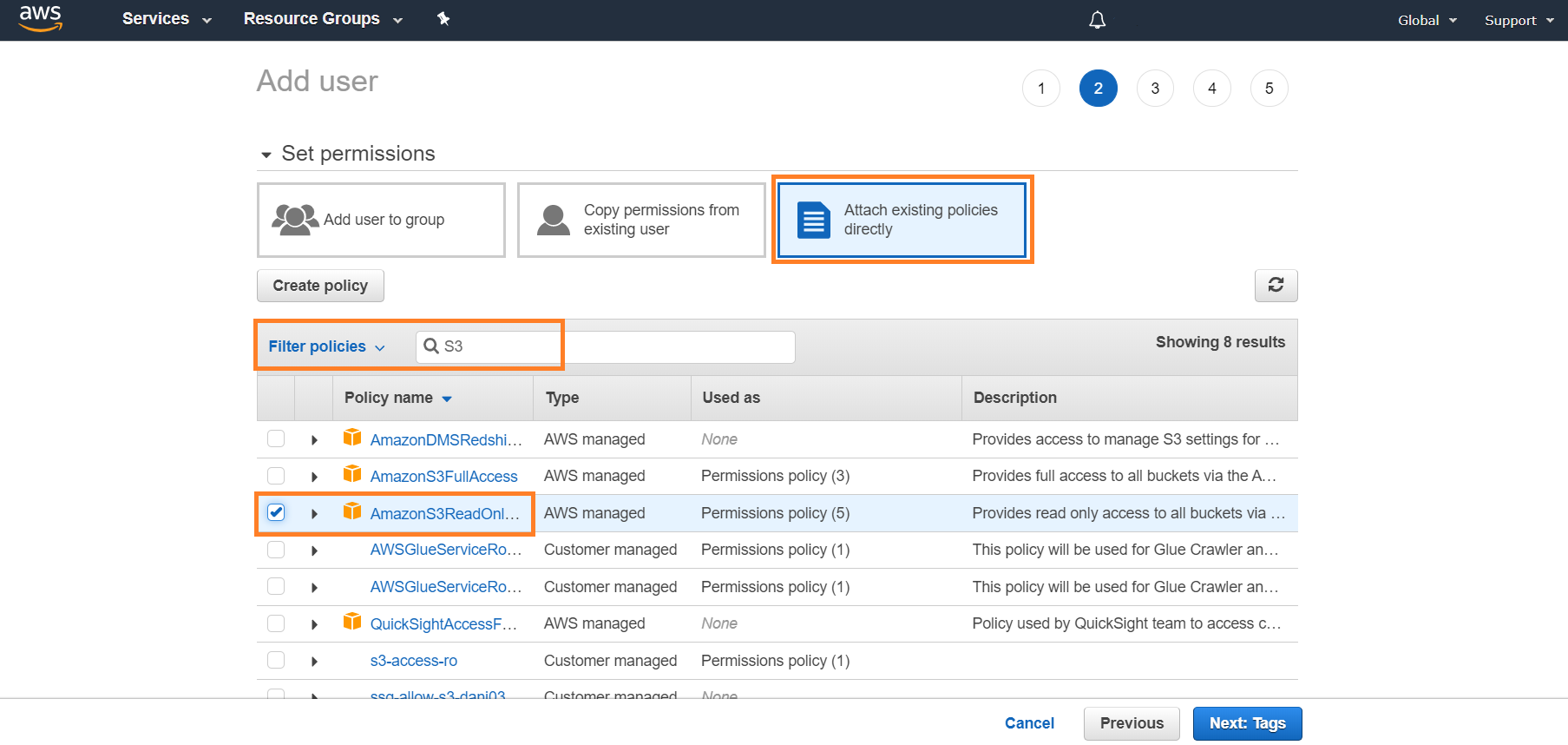
Import Imperva Incapsula Logs from S3
Log into your log relay server.
Navigate to the /opt/armor/log-relay/conf.d folder.
Create a new file using the following naming pattern: <pipeline_name>.<friendly_id>.env.
For example: pipeline-s3.incapsula.env
Pipeline name = "pipeline-s3"
Friendly_id (friendly name) = "incapsula"
Add the following content to the newly created .env file. This will be used to populate the template and create the pipeline.
CODE# The name of the S3 bucket bucket_name="example-bucket-name" # The region where the S3 bucket is provisioned region="example-region" # The type of logs being collected by this source log_type="imperva-incapsula" # The codec used to read the raw log files codec="line"After you have created the .env file and made any necessary changes, you will need to restart logstash.
systemctl restart armor-logstash
Verify Logs
In Nexus, hover over Threat Management
 on the left-side nav.
on the left-side nav.Click Log Search.
Then click Log Search tab on the top of the page.
Wait for the SSO.
In the Source column, review the source name to locate the newly created Imperva Incapsula remote log source.
In the search field, you can also enter "incapsula" to locate Imperva Incapsula messages.
Note: If you are using the Armor Management Portal (AMP), you can follow the same steps. Find Log Search under Armor Services in the Security section of the left-nav