Create a Remote Log Source - SecureSphere
Topics Discussed
You can use this document to add a remote log collector to a SecureSphere remote device (log source).
Pre-Deployment Considerations
Before you begin, review the following requirements:
Log Relay
For remote log collection, you must have a Log Relay server on your account.
To learn how to add Log Relay to your account, see Obtain Log Relay for Remote Log Collection.
Assumptions
The SecureSphere device is running at version v9.5 to v13 for Syslog in LEEF format
Your device is already configured and running the policies that are needed
You already have a log relay box set up and configured correctly
The security policies for any AWS security groups or firewalls allow traffic on port 10154 to reach the log relay
Update your Imperva SecureSphere Device
Log into your Imperva SecureSphere management console.
Navigate to Policies -> Action Sets
Click the Create New button to define a new action set
In the Action Name field, type a name for your alert action (ex: Log Firewall Alerts to Armor)
Select the appropriate event type from the Apply to Event Type dropdown menu - Options include Security Violations - All, Security Violations - Web Application Level, Security Violations - File Application Level, and System Events.
Click Create.
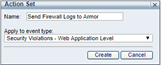
Configure the forwarding action
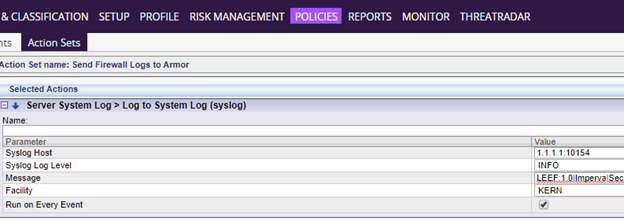
Click into your newly created action set
Under Available Action Interfaces, use the upward-pointing green arrow next to Server System Log > Log to System Log (syslog) to add the action interface to the Selected Interfaces section
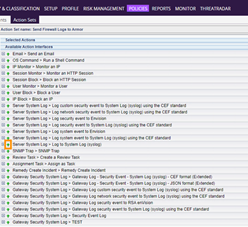
Expand the Action Interface just added to Selected Actions. In the Syslog Host field, enter the IP address of your Log Relay server and specify port 10154 using standard IP:PORT format (ex. 1.1.1.1:10154)
In the Syslog log level list, select INFO
In the Message field, paste the following, depending on the event type you are forwarding, and placing the appropriate date and time format your SecureSphere is configured for in devTimeFormat where listed :
For Security Violations - Web Application Level (v9.5 and v10 to v13):
LEEF:1.0|Imperva|SecureSphere|${SecureSphereVersion}|${Alert.alertType} ${Alert.immediateAction}|Alert ID=${Alert.dn}|devTimeFormat=|devTime=${Alert.createTime}|Alert type=${Alert.alertType}|src=${Alert.sourceIp}|srcPort=$!{Event.sourceInfo.sourcePort}|usrName=${Alert.username}|Application name=${Alert.applicationName}|dst=${Event.destInfo.serverIp}|dstPort=$!{Event.destInfo.serverPort}|Service name=${Alert.serviceName}|Event Description=${Alert.description}|Severity=${Alert.severity}|Simulation Mode=${Alert.simulationMode}|Immediate Action=${Alert.immediateAction}
For Security Violations - File Application Level (v9.5 and v10 to v13):
LEEF:1.0|Imperva|SecureSphere|${SecureSphereVersion}|${Alert.alertType} ${Alert.immediateAction}|Alert ID={Alert.dn}|devTimeFormat=|devTime=${Alert.createTime}|Alert type=${Alert.alertType}|src=${Alert.sourceIp}|usrName=${Event.struct.user.username}|Domain=${Event.struct.user.domain}|Application name=${Alert.applicationName}|dst=${Event.destInfo.serverIp}|Alert Description=${Alert.description}|Severity=${Alert.severity}|Immediate Action=${Alert.immediateAction}|SecureSphere Version=${SecureSphereVersion}
For Security Violations - Database Level(v9.5 and v10 to v13):
LEEF:1.0|Imperva|SecureSphere|${SecureSphereVersion}|${Alert.alertType} ${Alert.immediateAction}|Alert ID=${Alert.dn}|devTimeFormat=|devTime=${Alert.createTime}|Alert type=${Alert.alertType}|src=${Alert.sourceIp}|usrName=$ {Event.struct.user.user}|Application name=${Alert.applicationName}|dst=${Event.destInfo.serverIp}|Alert Description=${Alert.description}|Severity=${Alert.severity}|Immediate Action=${Alert.immediateAction}|SecureSphere Version=${SecureSphereVersion}
For System Events (v9.5 and v10 to v13):
LEEF:1.0|Imperva|SecureSphere|${SecureSphereVersion}|${Event.eventType}|Event ID=${Event.dn}|devTimeFormat=|devTime=${Event.createTime}|Event Type=${Event.eventType}|Message=${Event.message}|Severity=${Event.severity.displayName}|usrName=${Event.username}|SecureSphere Version=${SecureSphereVersion}
For All System Events (v6.2 and v7.x to v13 Release Enterprise Edition):
DeviceType=ImpervaSecuresphere Event|et=$!{Event.eventType}|dc=Securesphere System Event|sp=$!{Event.sourceInfo.sourcePort}|s=$!{Event.sourceInfo.sourceIp}|d=$!{Event.destInfo.serverIp}|dp=$!{Event.destInfo.serverPort}|u=$!{Event.username}|t=$!{Event.createTime}|sev=$!{Event.severity}|m=$!{Event.message}
For Database audit records (v9.5 and v10 to v13):
LEEF:1.0|Imperva|SecureSphere|${SecureSphereVersion}|${Event.struct.eventType}|Server Group=${Event.serverGroup}|Service Name=${Event.serviceName}|Application Name=${Event.applicationName}|Source Type=${Event.sourceInfo.eventSourceType}|User Type=${Event.struct.user.userType}|usrName=${Event.struct.user.user}|User Group=${Event.struct.userGroup}|Authenticated=${Event.struct.user.authenticated}|App User=${Event.struct.applicationUser}|src=${Event.sourceInfo.sourceIp}|Application=${Event.struct.application.application}|OS User=${Event.struct.osUser.osUser}|Host=${Event.struct.host.host}|Service Type=${Event.struct.serviceType}|dst=${Event.destInfo.serverIp}|Event Type=${Event.struct.eventType}|Operation=${Event.struct.operations.name}|Operation type=${Event.struct.operations.operationType}|Object name=${Event.struct.operations.objects.name}|Object type=${Event.struct.operations.objectType}|Subject=${Event.struct.operations.subjects.name}|Database=${Event.struct.databases.databaseName}|Schema=${Event.struct.databases.schemaName}|Table Group=$ {Event.struct.tableGroups.displayName}|Sensitive=${Event.struct.tableGroups.sensitive}|Privileged=${Event.struct.operations.privileged}|Stored Proc=${Event.struct.operations.storedProcedure}|Completed Successfully=${Event.struct.complete.completeSuccessful}|Parsed Query=${Event.struct.query.parsedQuery}|Bind Variables=${Event.struct.rawData.bindVariables}|Error=${Event.struct.complete.errorValue}|Response Size=${Event.struct.complete.responseSize}|Response Time=${Event.struct.complete.responseTime}|Affected Rows=${Event.struct.query.affectedRows}|devTimeFormat=|devTime=${Event.createTime}
In the Facility field, type syslog
Select the Run on Every Event check box
Click Save
Associate your policies to the new alert action:
From the navigation menu, click Policies -> Security
Select the policy that you want to use for the alert action
Click the Policy tab.
From the Followed Action list, select your new action (ex: Send Firewall Logs to Armor) and configure the parameters.
Ensure that your policy is configured as enabled and is applied to the appropriate server groups.
Click save.
Verify Connection
In Nexus, hover over Threat Management
 on the left-side nav.
on the left-side nav.Click Log Search.
Then click Log Search tab on the top of the page.
Wait for the SSO.
In the Source column, review the source name to locate the newly created SecureSphere remote log source.
In the search field, you can also enter "securesphere" to locate SecureSphere messages.
Note: If you are using the Armor Management Portal (AMP), you can follow the same steps. Find Log Search under Armor Services in the Security section of the left-nav
