Create Flow Connection - AWS VPC Flow Logs
Topics Discussed
To configure your account for remote log collection, you must have the following AMP permissions added to your account:
Delete Log Management
Read Log Endpoints
Write Log Endpoints
You can use this document to collect and send AWS VPC Flow Logs to Armor's Security Information & Event Management (SIEM).
For details about support for AWS Enriched VPC Flow Logs, contact Armor Support
Pre-Deployment Considerations
Before you begin, review the following requirements.
Prerequisites
Armor Account ID
AMP Permissions
Your Armor Management Portal (AMP) account must have the following permissions:
Delete Log Management
Read Log Endpoints
Write Log Endpoints
To learn more about permissions in AMP, see Roles and Permissions.
Flow Source
A flow source is required in order to ingest flow data in the Armor SIEM. The flow source will be dedicated to your flow data. You will not be charged until data begins to flow into the Armor SIEM.
Complete the following steps here to enable flow collection for your account.
Webhook Tagging
To learn more about Webhook Tagging for Flow logs, see the article here.
AWS account permissions (policies)
Your AWS service account must have full access to AWS CloudWatch.
Your individual AWS user account must have full access to the following AWS features:
AWS VPC
AWS Lambda
AWS CloudWatch
AWS CloudFormation
AWS Components
The AWS components that will be used are:
S3
IAM
Lambda
VPC Flow Logs
Armor does not provide support for using AWS CloudFormation to set up AWS VPC Flow Log resources in AWS GovCloud (US).
Configure the AWS VPC Flow Log CloudFormation Stack Template
You can use these instructions to collect and send logs from a single VPC Flow Log.
Login into the AWS console.
Go to the CloudFormation service.
Click Create stack.
The CloudFormation template used to implement the integration deploys a lambda function outside of a VPC. If the template is modified to deploy the armor-vpc-flow-lambda-... lambda function in a VPC, the https://1d.log.armor.com:5443 endpoint will need to be made accessible.
In the AWS console, in the top menu, on the right side, select the desired region for log collection.
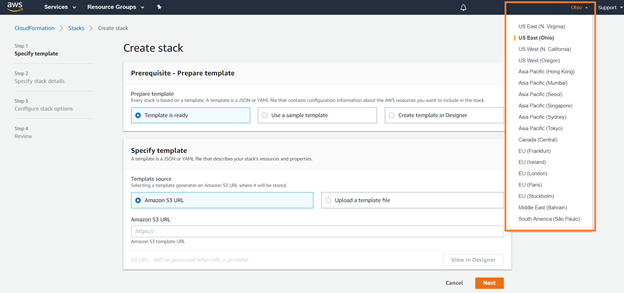
In Specify an Amazon S3 template URL, input the following link: https://s3-us-west-2.amazonaws.com/logs.armor.com/log-relay-aws-vpc-flows/log-relay-aws-vpc-flows.yaml.
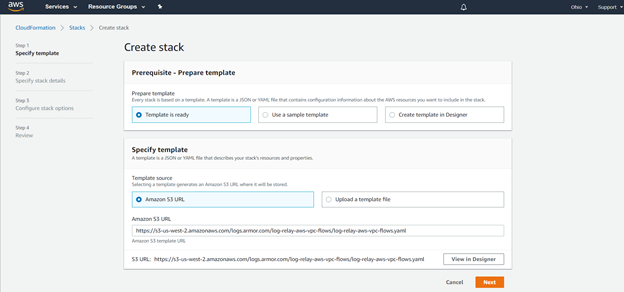
Click Next.
In Stackname, enter a descriptive name.
This name must begin with a letter, and can only contain letters, numbers, and hyphens.
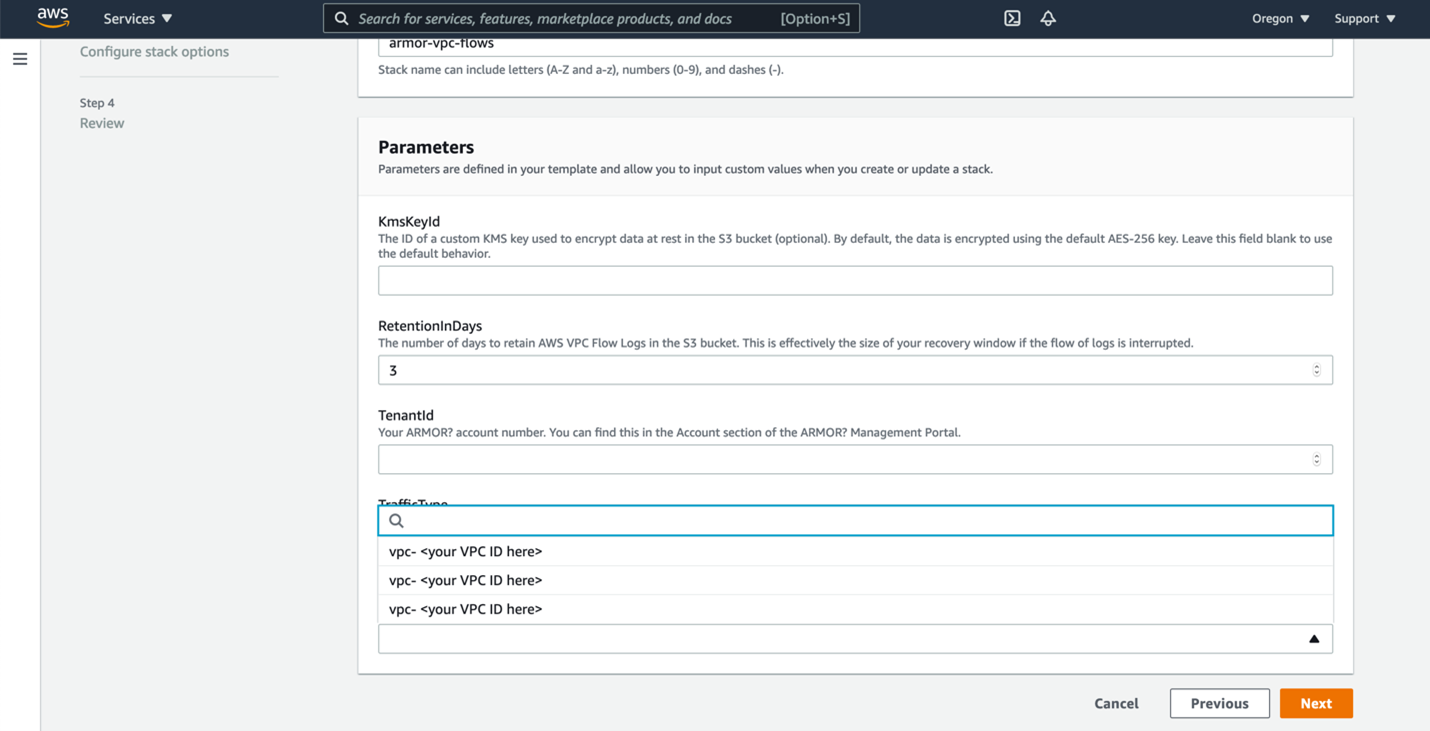
(Optional) In KmsKeyStack, enter the customer KMS key stack (if applicable).
By default, the logs will be stored in s3 with AES256 encryption.
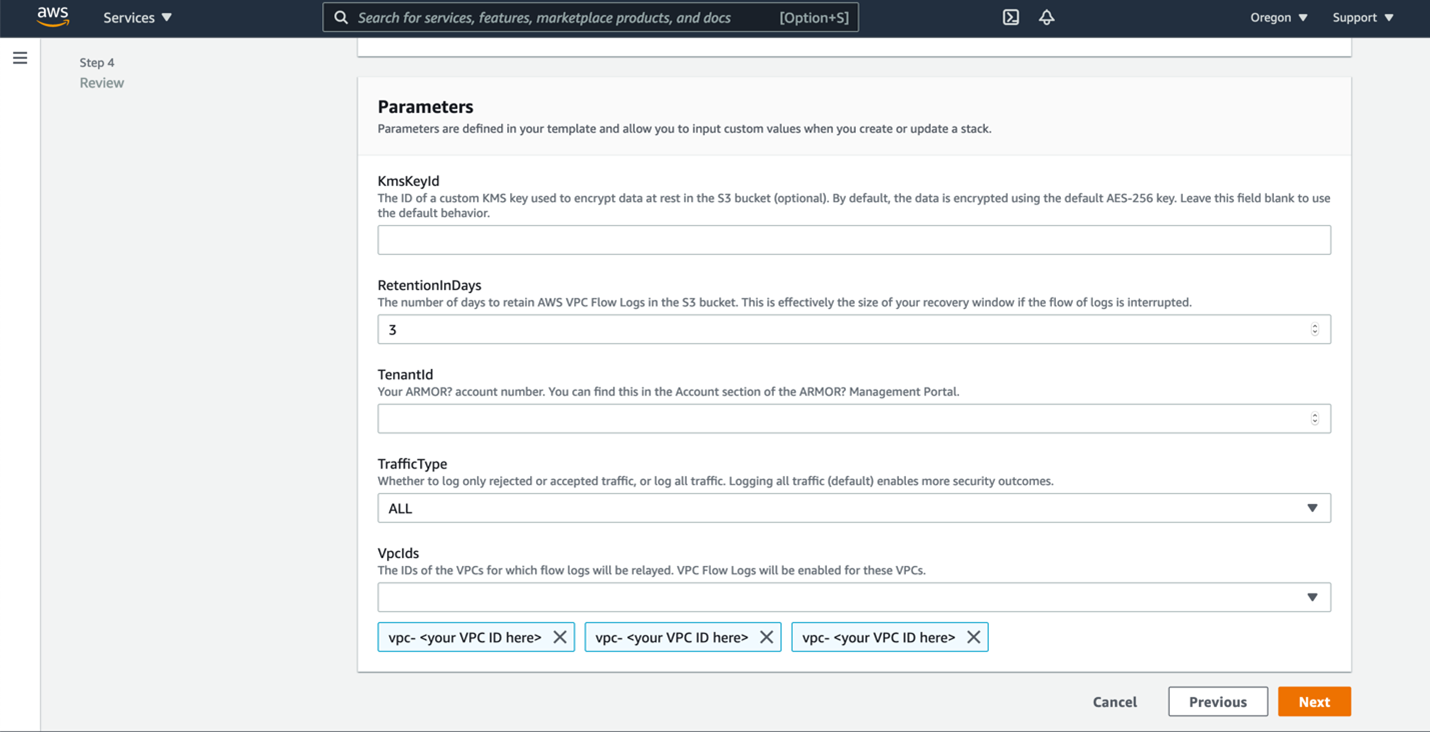
In RetentionInDays, enter the number of days to retain the log files in the S3 bucket.
By default, Armor has configured 3 days; set to 0 to keep logs until manually removed.
In TenantId, enter your Armor account number.
This can be found in the AccountOverview section of your AMP account.
In TrafficType, select the type of traffic to log:
ALL - Capture all traffic (default); recommended
Accept - Capture the VPC accepted traffic
Reject - Capture the VPC rejected traffic
In VpcId, select the ID of the VPC for which the flow log will be relayed.
Select all VPC IDs for this account (within the account's region) that you would like to ingest.
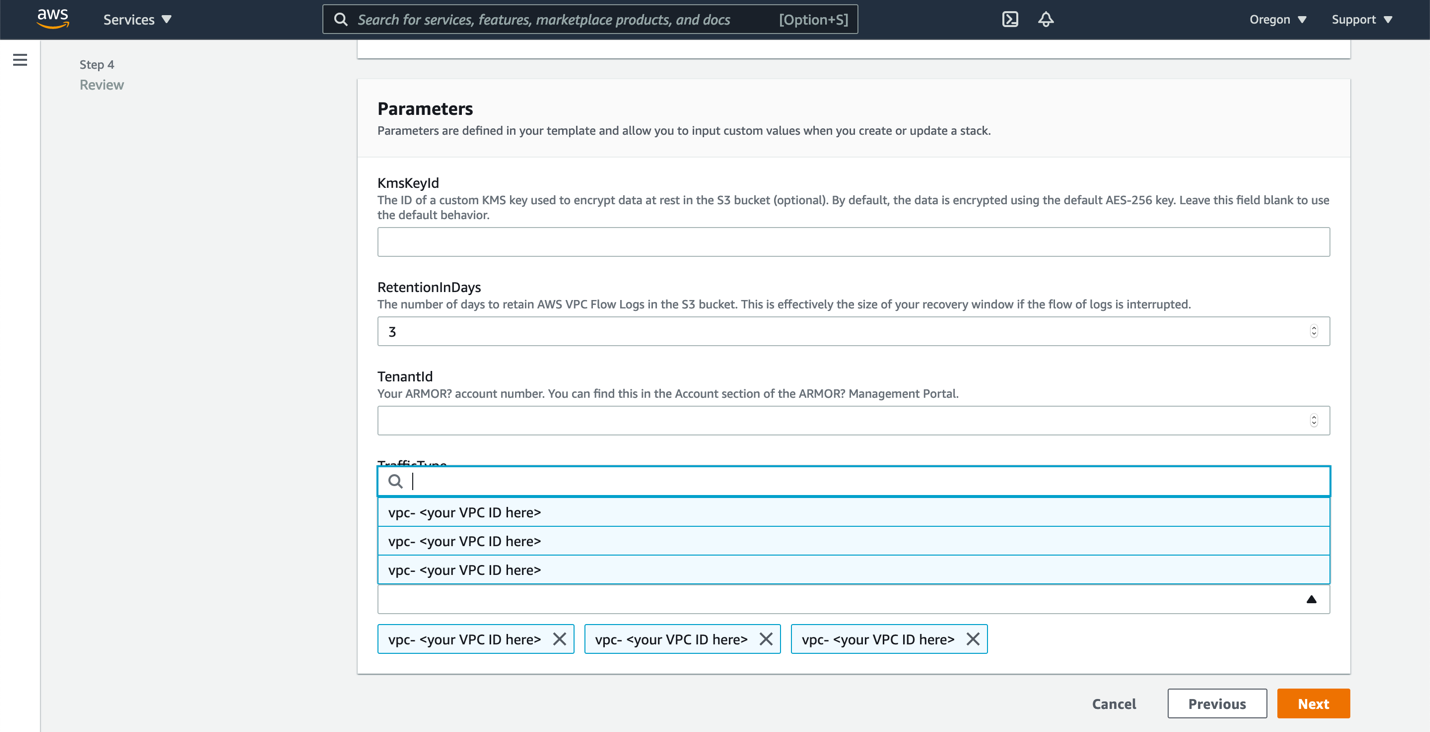
Click Next.
Click Next.
At the bottom of the screen, mark the box to accept the terms, and then click Create.
(Optional) Click the Refresh button to see the status of the stack creation.
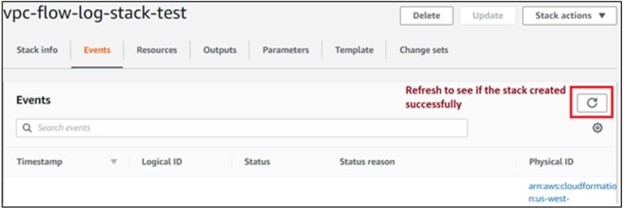
You can verify that the stack was created successfully on the Resources
Following successful deployment of the CloudFormation stack, the collected AWS VPC Flow Logs are visible from Log Search on average in 15 minutes and up to 30 minutes.
Verify Connection
In Nexus, hover over Threat Management
 on the left-side nav.
on the left-side nav.Click Log Search.
Then click Log Search tab on the top of the page.
Wait for the SSO.
Click Discover to take you to the log search screen.
Review the source name to locate the newly created AWS VPC Flow Log remote log source.
In the search field, you can also enter the AWS acccount ID to locate AWS VPC Flow Log messages.
Edit a Stack
This section only applies to single stacks, not stack sets.
Currently, Armor's AWS CloudFormation template does not support updates. If you want to update your stack, then you must delete the remote log source, and then create a new one with your desired updates.?
Migrate from Log Relay
The Armor Log Relay is no longer required to collect and monitor AWS VPC Flow Logs. Deploying a stack using the most recent CloudFormation template will provision a new integration that sends logs directly to Armor.
