Export Custom Rules
This guide covers how to export custom rules that are already deployed on Sentinel and how to test them.
Export rules from Sentinel to JSON
If you have yet to create a custom rule, please refer to the following guide by Microsoft. Create custom analytics rules to detect threats. Once done, follow the steps described below.
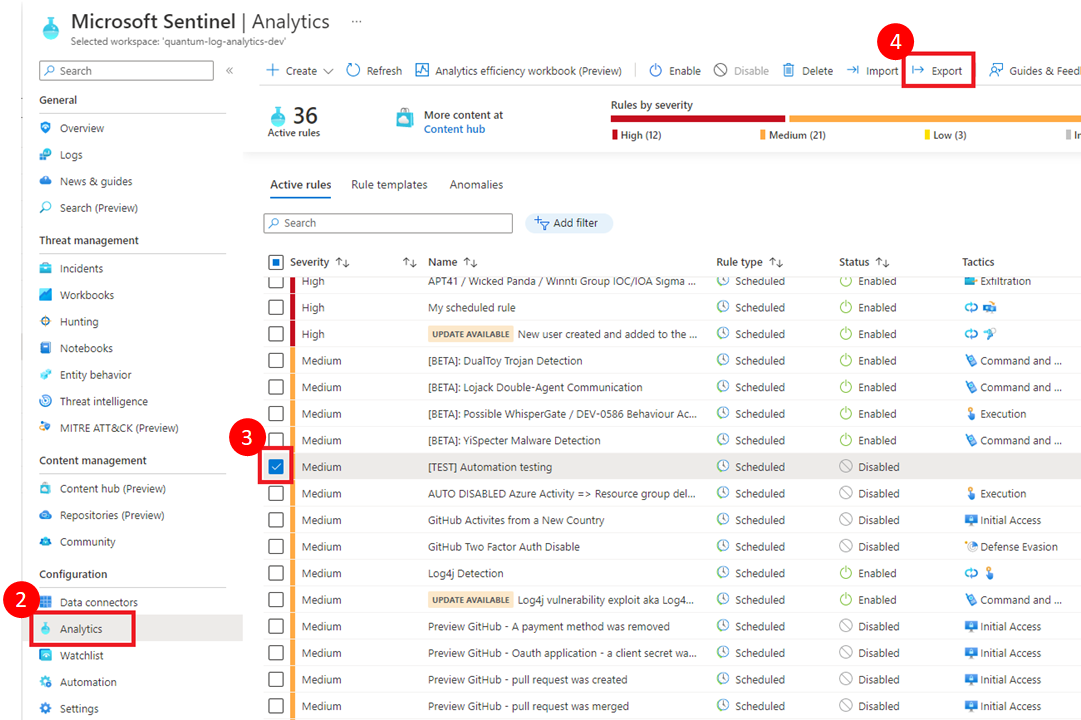
- Navigate to your Sentinel workspace
- Click on Analytics
- Check the checkbox for the custom rule you wish to export
- Click on “Export” button at the top
Convert rules from JSON to yaml
To convert the rules from JSON to yaml manually. Please refer to the example below for the format and fill in accordingly.
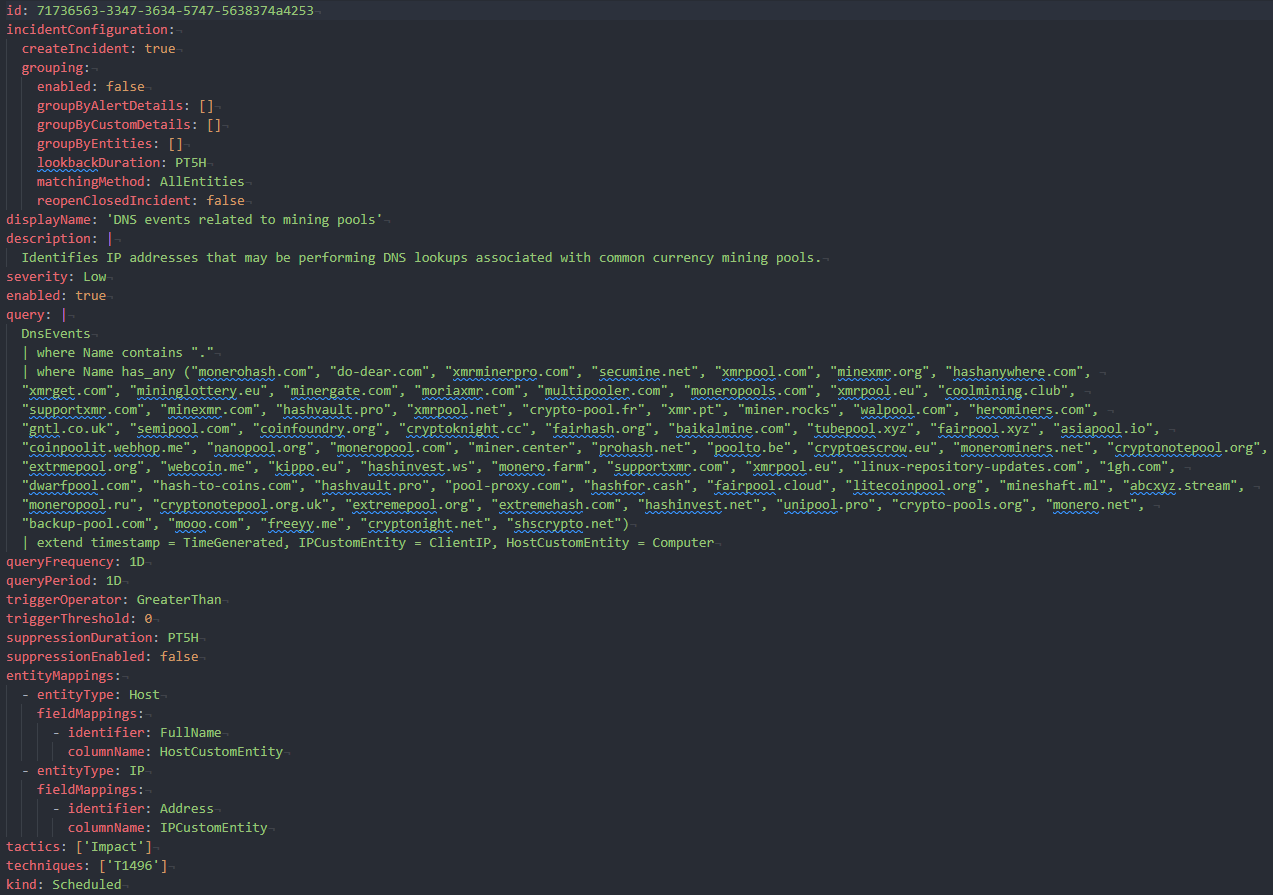
Text format to copy paste
id: 71736563-3347-3634-5747-5638374a4253
incidentConfiguration:
createIncident: true
grouping:
enabled: false
groupByAlertDetails: []
groupByCustomDetails: []
groupByEntities: []
lookbackDuration: PT5H
matchingMethod: AllEntities
reopenClosedIncident: false
displayName: 'DNS events related to mining pools'
description: |
Identifies IP addresses that may be performing DNS lookups associated with common currency mining pools.
severity: Low
enabled: true
query: |
DnsEvents
| where Name contains "."
| where Name has_any ("monerohash.com", "do-dear.com", "xmrminerpro.com", "secumine.net", "xmrpool.com", "minexmr.org", "hashanywhere.com",
"xmrget.com", "mininglottery.eu", "minergate.com", "moriaxmr.com", "multipooler.com", "moneropools.com", "xmrpool.eu", "coolmining.club",
"supportxmr.com", "minexmr.com", "hashvault.pro", "xmrpool.net", "crypto-pool.fr", "xmr.pt", "miner.rocks", "walpool.com", "herominers.com",
"gntl.co.uk", "semipool.com", "coinfoundry.org", "cryptoknight.cc", "fairhash.org", "baikalmine.com", "tubepool.xyz", "fairpool.xyz", "asiapool.io",
"coinpoolit.webhop.me", "nanopool.org", "moneropool.com", "miner.center", "prohash.net", "poolto.be", "cryptoescrow.eu", "monerominers.net", "cryptonotepool.org",
"extrmepool.org", "webcoin.me", "kippo.eu", "hashinvest.ws", "monero.farm", "supportxmr.com", "xmrpool.eu", "linux-repository-updates.com", "1gh.com",
"dwarfpool.com", "hash-to-coins.com", "hashvault.pro", "pool-proxy.com", "hashfor.cash", "fairpool.cloud", "litecoinpool.org", "mineshaft.ml", "abcxyz.stream",
"moneropool.ru", "cryptonotepool.org.uk", "extremepool.org", "extremehash.com", "hashinvest.net", "unipool.pro", "crypto-pools.org", "monero.net",
"backup-pool.com", "mooo.com", "freeyy.me", "cryptonight.net", "shscrypto.net")
| extend timestamp = TimeGenerated, IPCustomEntity = ClientIP, HostCustomEntity = Computer
queryFrequency: 1D
queryPeriod: 1D
triggerOperator: GreaterThan
triggerThreshold: 0
suppressionDuration: PT5H
suppressionEnabled: false
entityMappings:
- entityType: Host
fieldMappings:
- identifier: FullName
columnName: HostCustomEntity
- entityType: IP
fieldMappings:
- identifier: Address
columnName: IPCustomEntity
tactics: ['Impact']
techniques: ['T1496']
kind: Scheduled
Note
Please take special note on the entity mapping and refer to this document to understand better and the best practices
Test custom yaml rules
Once you have converted the rules, you can now perform testing to check if they will be deployed correctly.
Set up testing environment
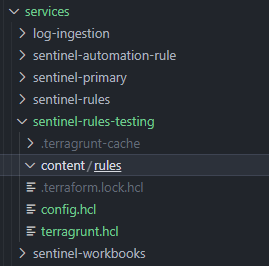
- Clone infrastructure-live repository
- Change directory to
azure/dev/southeastasia/<prefix>-log-analytics/services/ - Create a new folder under the above directory. e.g
sentinel-rules-testing - Copy
config.hclandterragrunt.hclfrom thesentinel-rulesfolder - Create a new directory within the current folder
content/rules - In the newly copied
config.hclremove the comment from# content_path_rules = "content/rules"
The final folder structure should look like this
Add custom rules into testing environment
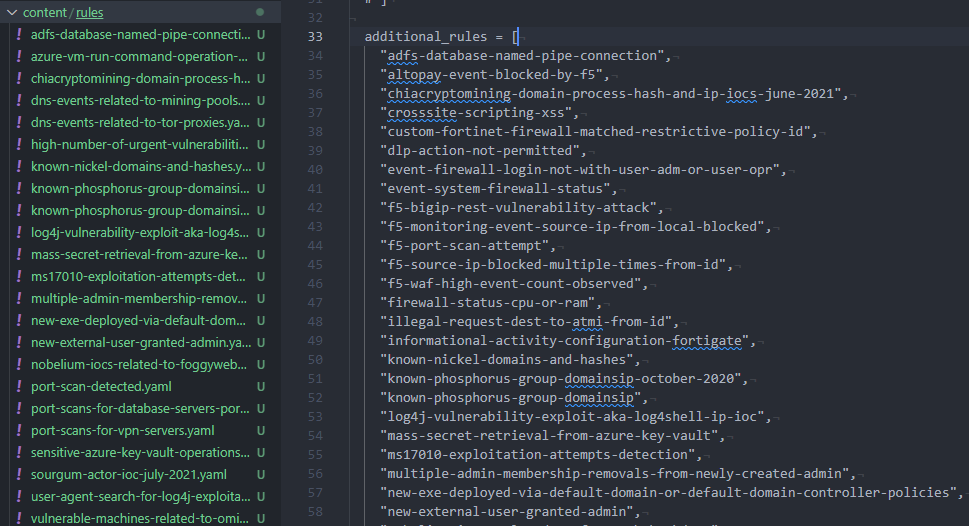
- Move/copy all custom yaml rules into the
content/rulesfolder you have just created - Open
config.hcland under theadditional_rulesfield add in each of the custom rules
It should be look similar to this
Please note that if you have specified a different content_path_rules you will have to follow that instead.
Logg into Azure and setting subscription
- In your terminal, run
az loginand select the appropriate account - Once signed in, run
az account set --subscription <SUBSCRIPTION_ID>to set your subscription.
Run test
- In your terminal, change directory to
sentinel-rules-testing - Run
terragrunt plan - Fix any errors that is reported and run the above command again
- Once fixed, run
terragrunt apply - If the results looks desirable, enter
yeswhen prompted - Open up Sentinel and check if your custom rules have successfully deployed
Clean up
Once your testing is complete, clean up the Sentinel by running terragrunt destroy to delete the newly created custom rules on Sentinel
If you wish to deploy these on customer environment please refer correct guide below.
- Deploying rules that are specific to certain customers
- Deploying rules that are generic to all customers
Potential Errors and Solutions
This section covers some of the potential errors that you may face and how to resolve them.
Backend initialization required, please run “terraform init
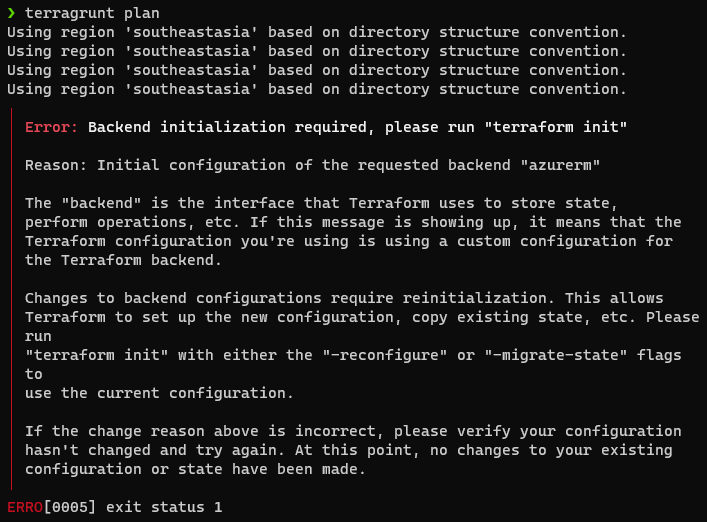
Please check if you are logged into the correct Azure account with the correct subscription set.
If the error still persist, run az logout and sign in by following Logging into Azure and setting subscription
Module source has changed
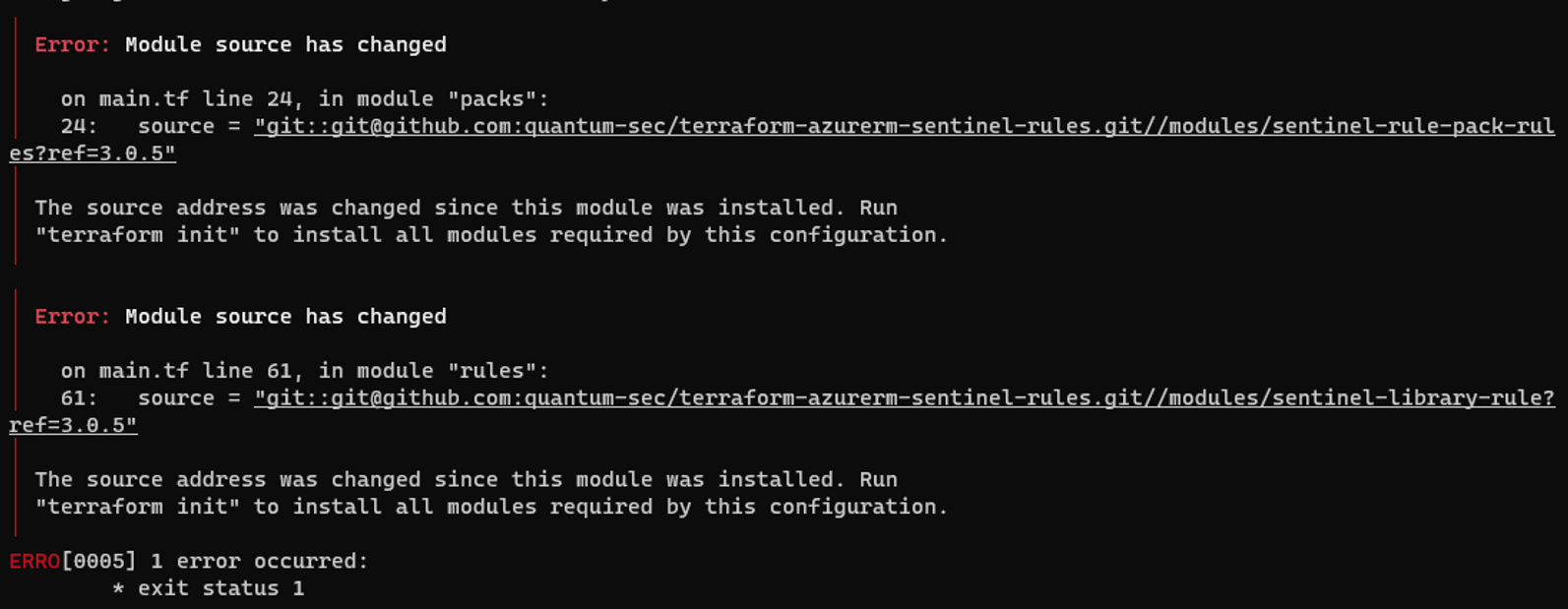 Run the following command
Run the following command
terragrunt initDebug Terragrunt
If the error you are facing is not one of the above, you can execute the following command to enable debugging.
terragrunt plan --terragrunt-log-level debug --terragrunt-debug
