Toolbox
Overview
The Toolbox is a self service tool accessing a combination of services that allows customers to remotely manage services on one or multiple Virtual Machines on an account. Below are how to steps for using the toolbox as well as descriptions of the services you can manage with the toolbox.
Users looking to deploy services at scale can use the Toolbox to schedule tasks for a fleet of assets in their environment.
How to Schedule a Task
Users can access the Schedule Task Screen from the Toolbox in either Nexus or the legacy Armor Management Portal (AMP). Once a task is scheduled, the page will display all pending and completed tasks. The Schedule Task button is available at the top of the screen. For more details about the Toolbox screen, [click here].
In Nexus, the Toolbox screen can be found under the Security Posture
 section, within the Endpoint category.
section, within the Endpoint category.In the Armor Management Portal (AMP), the Toolbox screen is located under the Infrastructure section.
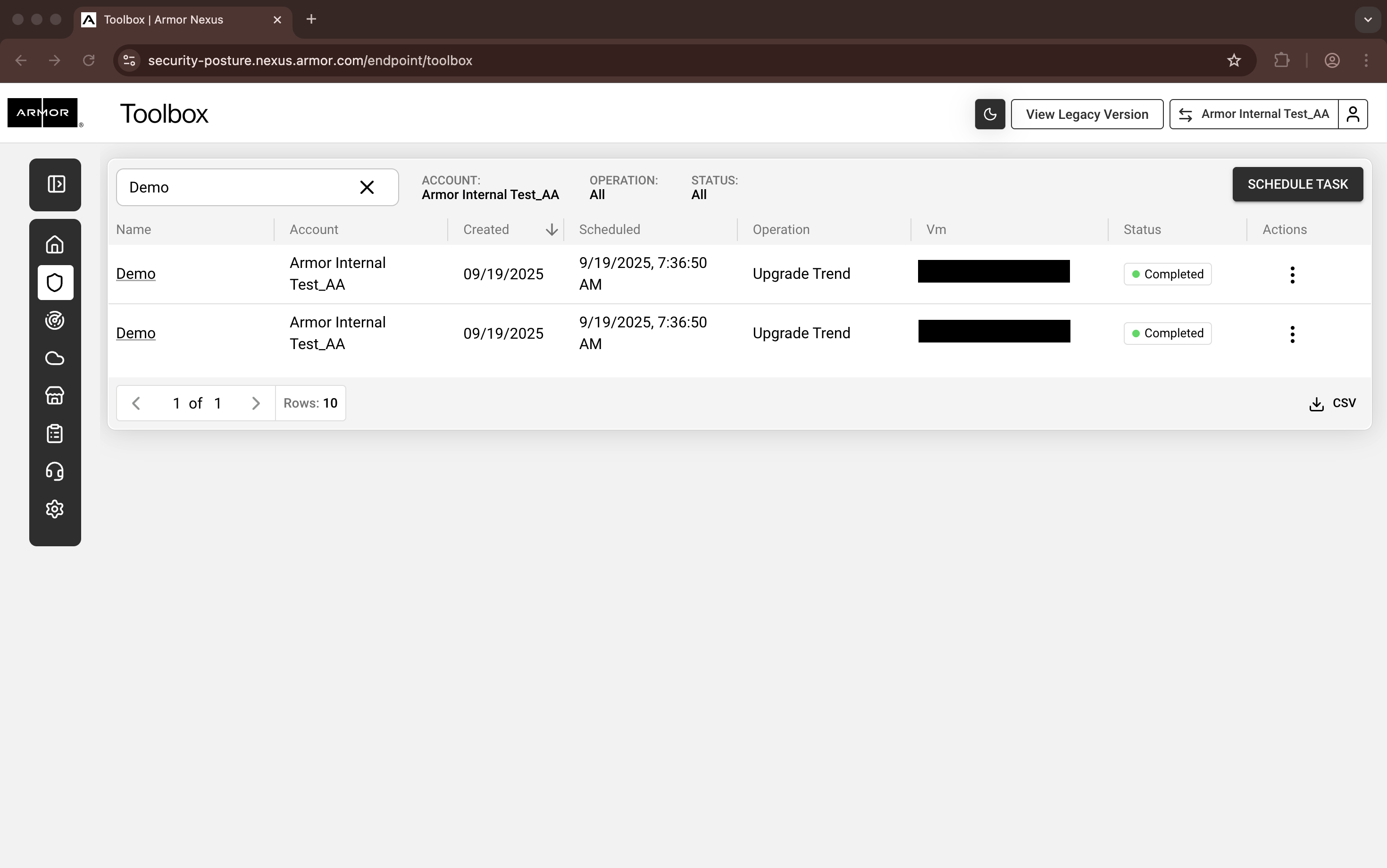
Toolbox - Nexus
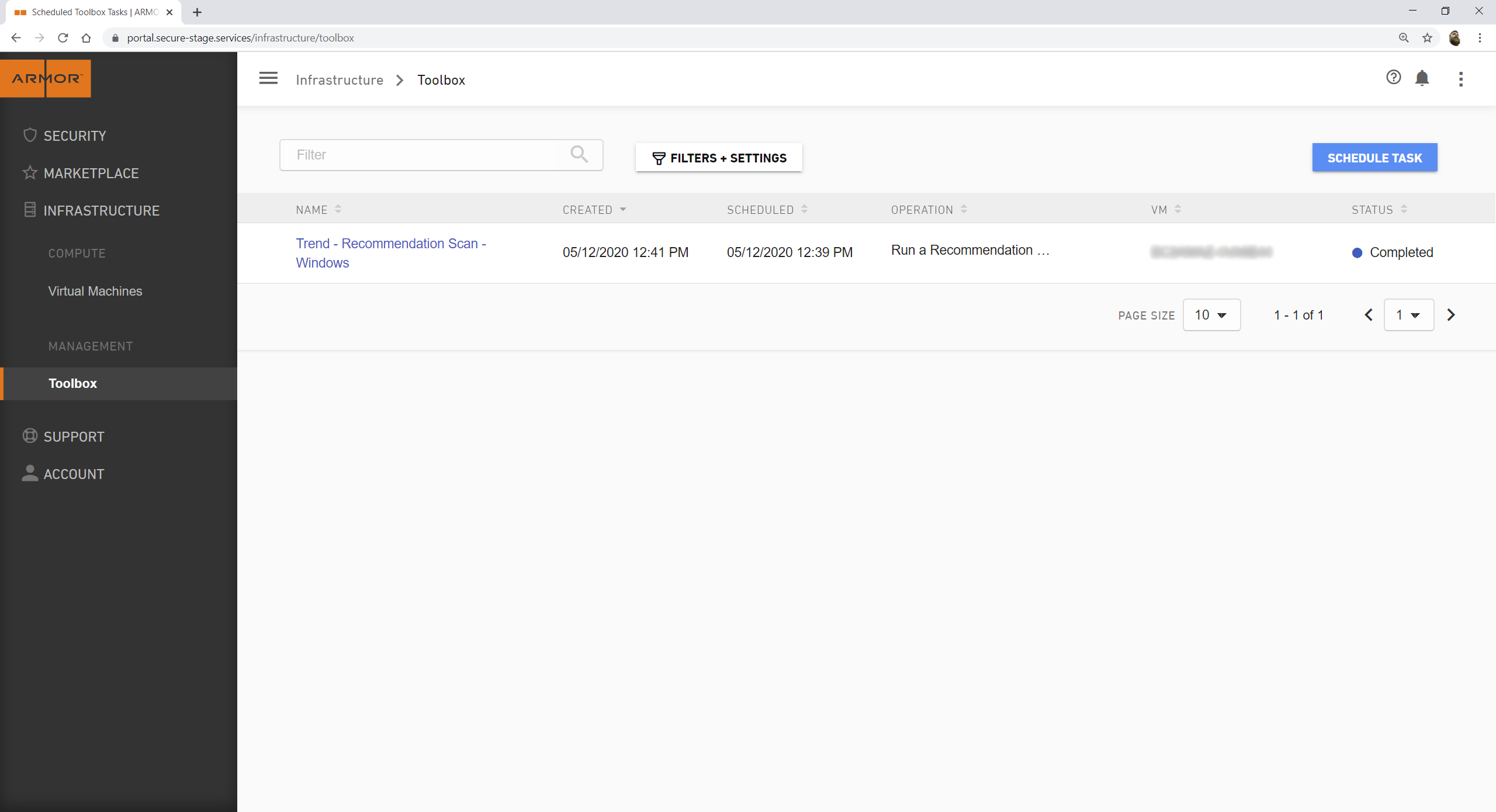
Toolbox - Armor Management Portal (AMP)
Navigate to the Toolbox screen.
Click Schedule Task.
Click the Product drop-down and select the desired Armor Security Service.
Click the Operation drop-down and select the desired operation.
If necessary, enter additional configuration parameters in the Additional Configuration text box.
Enter a task name in the Task Name field.
Click Schedule Future Date to select the task date.
Unless configured otherwise, all tasks will run at the next Agent Heartbeat (every 15 minutes).
Click Select VMs button.
Select the appropriate Virtual Machines using the check boxes.
Click Select VMs.
Select VMs.
Confirm the selected VMs by clicking on Select VMs.
Click Schedule Task.
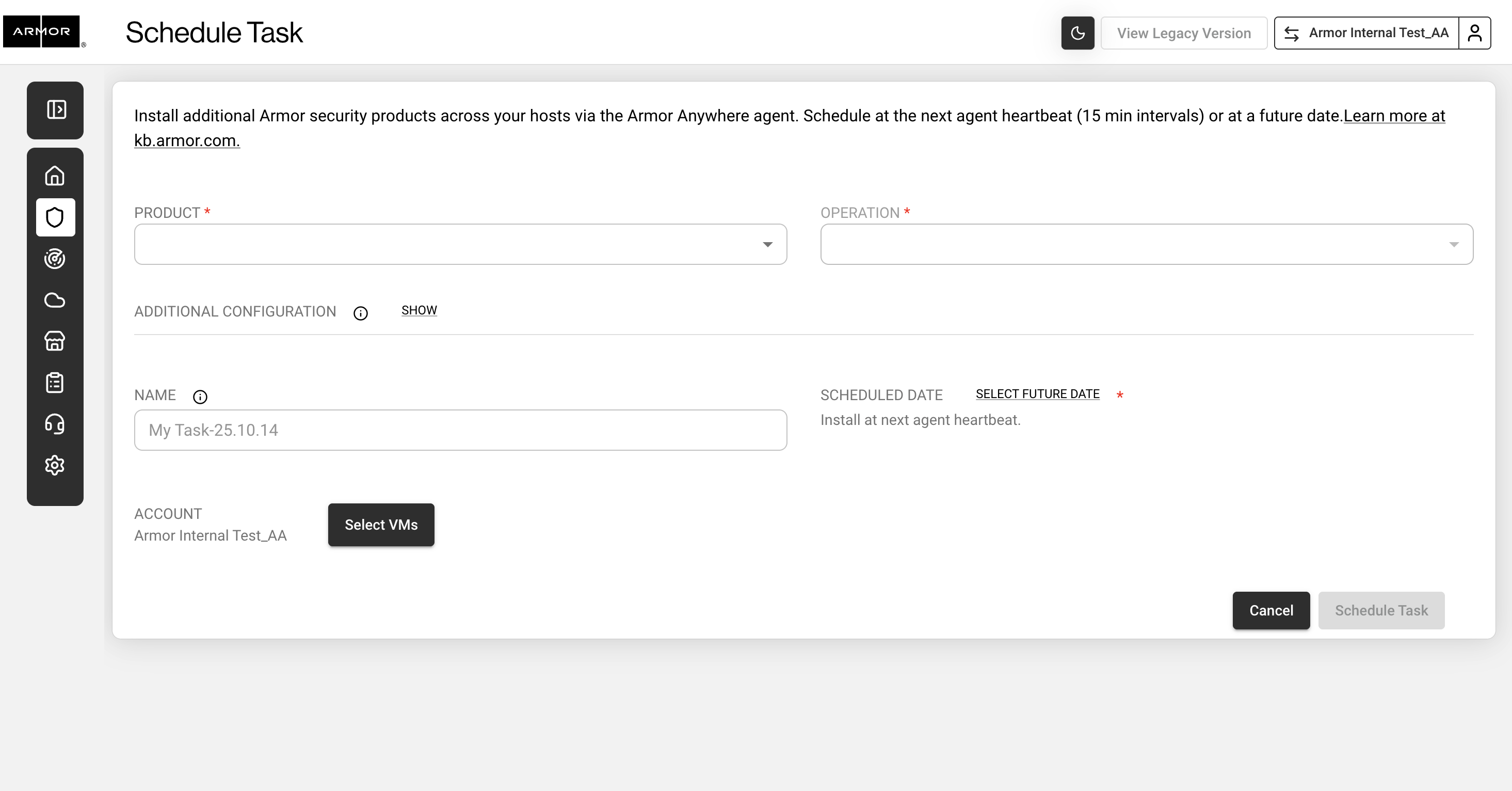
Schedule Task - Nexus
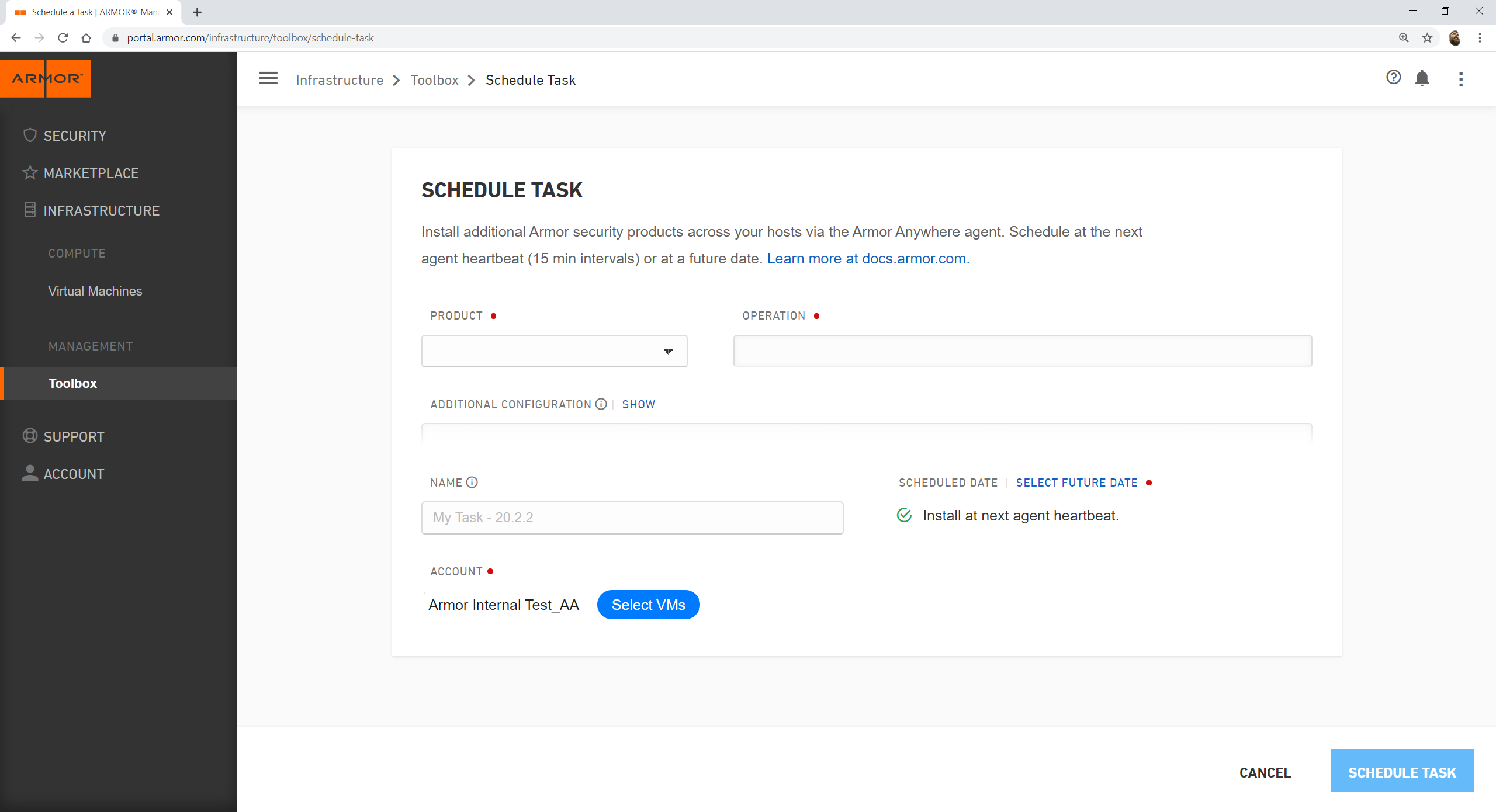
Schedule Task - Armor Management Portal (AMP)
Asynchronous Security API Calls
Users may want to configure security services asynchronously so that security services can be activated without immediately triggering feedback. For some commands, users can use the flag async=true to queue these features as needed. The command async=true works for both Windows and Linux and should be placed at the end of the command line as shows in the example below:
Windows: C:\.armor\opt\armor.exe av on async=true
Linux: /opt/armor/armor av on async=trueThe async flag can also be configured in the Armor Toolbox.
Review Task Results
Users can check the status and results of scheduled tasks in two ways:
Option 1: From the Toolbox Screen
Navigate to the Toolbox screen.
Locate the task by the name it was created under.
The screen will display both pending and completed tasks.
Option 2: From a Specific Virtual Machine
Go to the Virtual Machines screen:
This is located under Infrastructure > Compute.
Select the desired VM to view its details.
Navigate to the CLI Results tab to see the output of tasks executed on that VM.
Security Services
Below are the Armor Security Services you can manage from the Armor Toolbox. Several operations can be run asynchronously to prevent immediate API feedback. For more information on the Async Flag, please see the documentation above.
Trend
Trend is the parent sub-agent for all Trend modules, including Malware Protection, File Integrity Monitoring, and Intrusion Prevention.
One of the features available in Agent 3.0 is Recommendation scans. Recommendation scans provide a good starting point for establishing a list of rules that you should implement. During a recommendation scan, the Armor Agent scans the operating system for installed applications, the Windows registry, open ports, and more.
In order to use Malware Protection, File Integrity Monitoring, and Intrusion Prevention, please install the Trend Sub-Agent. To take advantage of Recommendation scans, turn on Ongoing Recommendation scans in the Toolbox.
Operation | Description | Async Flag |
|---|---|---|
trend install | Install Trend | |
trend uninstall | Uninstall Trend | |
trend status | Agent Status | |
trend kernel-check | Check if the Linux distribution kernel is supported | |
trend ongoing-recommendation-scan on | Turn On Ongoing Recommendation scan | Yes |
trend ongoing-recommendation-scan off | Turn Off Ongoing Recommendation scan | Yes |
trend recommendation-scan | Schedule a Recommendation Scan | Yes |
trend set-recommendation-scan-interval | Set the Recommendation Scan Interval | Yes |
.Malware Protection
The Armor Malware Protection service protects your Virtual Machines against file-based threats such as malware, viruses, and more.
To use this feature, select the Malware Protection product in the Toolbox and choose the "on" operation.
Operation | Description | Async Flag |
|---|---|---|
av on | Turn anti-malware protection on | Yes |
av off | Turn anti-malware protection off | Yes. |
av status | Reports status of module from subagent |
File Integrity Monitoring
The Armor File Integrity Monitoring service detects changes to files and critical system areas (e.g. Windows registry) that could indicate suspicious activity. If you have enabled Recommendation scans (Trend sub-agent), you can run Recommendation scans with FIM to identify a list of rules that should be applied based on the configuration of your Virtual Machine. You can also choose to have the recommended rules automatically applied to your machine.
To use this feature, select the FIM product in the Toolbox and choose the "on" operation. To use this feature with Recommendation scans, select the FIM product in the Toolbox and choose the "auto-apply-recommendations-on" operation.
Operation | Description | Async Flag |
|---|---|---|
fim on Optional Parameter: fim on auto-apply-recommendations=on fim on auto-apply-recommendations=off | Turn file integrity monitoring on Auto-apply recommendations on Auto-apply recommendations off | Yes Yes Yes |
fim off | Turn file integrity monitoring off | Yes |
fim list-available-rules | List available rules | |
fim list-assigned-rules | List assigned rules | |
fim assign-rules | Assign rules | Yes |
fim unassign-rule | Unassign rule | Yes |
fim add-custom-filepath-rule | Add custom filepath | |
fim update-custom-filepath-rule | Update custom filepath | |
fim delete-custom-filepath-rule | Delete custom filepath | |
fim get-custom-filepath-rule | Get custom filepath | |
fim status | Reports status of module from subagent |
.Intrusion Prevention System
The Armor Intrusion Prevention System service detects or prevents known and zero-day vulnerabilities (e.g. SQL injections attacks, cross-site scripting attacks, etc). Customers can use IPS in prevent or detect mode, depending on whether you want traffic to be blocked or not. If you have enabled Recommendation scans (Trend sub-agent), you can run Recommendation scans with IPS to identify a list of rules that should be applied based on the configuration of your Virtual Machine. You can also choose to have the recommended rules automatically applied to your machine.
To use this feature, select the IPS product in the Toolbox and choose the "prevent" or "detect" operation. To use this feature with Recommendation scans, select the IPS product (prevent or detect mode) in the Toolbox and choose the "auto-apply-recommendations-on" operation.
Operation | Description | Async Flag |
|---|---|---|
ips detect Optional Parameter: ips detect auto-apply-recommendations=on ips detect auto-apply-recommendations=off | Turn intrusion prevention on in detect mode Auto-apply recommendations on Auto-apply recommendations off | Yes Yes Yes |
ips prevent Optional Parameter: ips prevent auto-apply-recommendations=on ips prevent auto-apply-recommendations=off | Turn intrusion prevention on in prevent mode Auto-apply recommendations on Auto-apply recommendations off | Yes Yes Yes |
ips off | Turn intrusion prevention off | Yes |
ips list-assigned-rules | List assigned rules | Yes |
ips assign-rules | Assign rules | Yes |
ips unassign-rule | Unassign rule | |
ips status | Reports status of module from subagent |
.Vulnerability Management
Armor's Vulnerability Scanning service detects OS and application vulnerabilities present in your environment.
To use this feature, select the Vulnerability Management product in the Toolbox and choose the "on" operation.
Operation | Description |
|---|---|
vuln install | Install Qualys vulnerability management |
vuln uninstall | Uninstall Qualys vulnerability management |
.
Logging
The Armor Logging service ships OS logs to Armor for correlation and analysis.
To use this feature, select the Logging product in the Toolbox and choose the "on" operation.
Operation | Description |
|---|---|
logging install | Install logging service |
logging uninstall | Uninstall logging service |
By default, the Armor Agent collects the following logs for 30 days:
CentOS/RHEL | Ubuntu/Debian | Windows |
|---|---|---|
/var/log/secure /var/log/messages /var/log/audit.log /var/log/yum.log | /var/log/auth.log /var/log/syslog | System Event Log Security Event Log |
Log Relay
To use this feature, select the Log Relay product in the Toolbox and choose the "install" operation.
Operation | Description |
|---|---|
relay install | Install Log Relay Software |
relay uninstall | Uninstall Log Relay Software |
Additional Services
Tags
Armor's Tagging feature allows users to add metadata tags to their logs. Users can search for these tags via the API, or through Nexus or the legacy Armor Management Portal (AMP) on the Virtual Machines screen.To use this feature, select the Tags product in the Toolbox and choose the "create tags" operation. In the Additional Configuration text box, enter a key value pair (e.g. key=pair). You can enter more than one tag using a comma as separator.
Operation | Description |
|---|---|
create-tags | Create Tags |
delete-tags | Delete Tags |
describe-tags | Describe tags |
Communication Check
The communication-check operation is used to validate outbound connectivity from a customer’s VM to specified hosts and ports. This operation helps ensure that services such as Trend Vision One are reachable and functioning correctly.
armor communication-check <host1[:port1]>,<host2[:port2]>,...Examples:
Windows: C:\.armor\opt\armor.exe agent communication-check agents.deepsecurity.trendmicro.com,us-west.epsec.secure-prod.services:4120,workload.us-1.cloudone.trendmicro.com
Linux: /opt/armor/armor agent communication-check agents.deepsecurity.trendmicro.com,us-west.epsec.secure-prod.services:4120,workload.us-1.cloudone.trendmicro.comToolbox example:
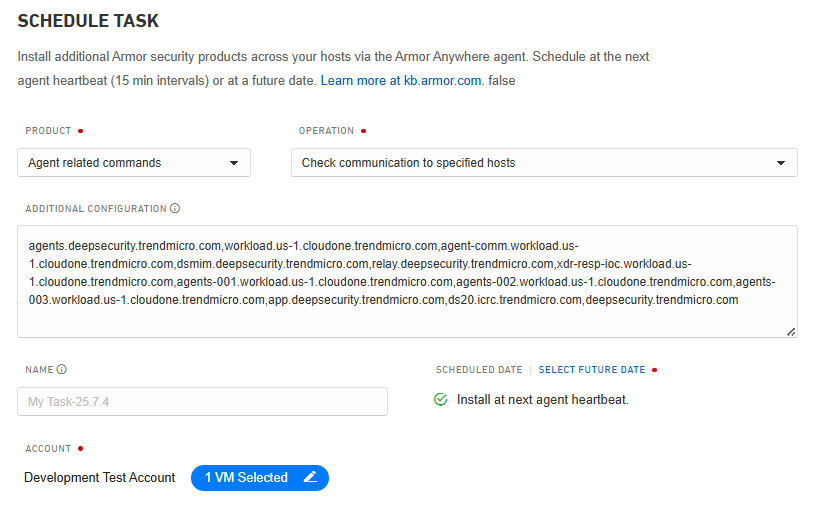
SSL Check
This command will check servers used by the agent for connectivity. SSL-check command will check all services regardless of if a particular service is installed on them or not. This feature is primarily for debugging and informational purposes. Command is valid for both Windows and Linux operating systems.
Operation | Description |
|---|---|
armor agent ssl-check | checks servers for connectivity |
Remediate
This command will perform on-demand remediation of security subagent services by checking their installation and runtime status, restarting them if necessary, and verifying connectivity to their respective servers. It also validates TLS certificates and automatically renews them if found invalid—updating the system’s trust store as needed. Each action is logged for visibility and traceability. This ensures critical agent services are functional and securely connected, reducing downtime and manual troubleshooting efforts.
Operation | Description |
|---|---|
armor agent remediate | Checks subagent services and connectivity, and attempts remediation if issues are found. |
Sysmon
Configuring Apache services uses the Command Line Interface (CLI) feature. For more information, see Security Service CLI Commands.
The following arguments to install and uninstall Sysmon services.
COMMAND | ARGUMENTS | RESULT |
|---|---|---|
sysmon | install | Installs the Sysmon service. |
sysmon | uninstall | Removes the Sysmon service. |
The following arguments are possible parameters for the Logging CLI feature.
COMMAND | ARGUMENTS | RESULT |
|---|---|---|
add-event-logs | "Microsoft-Windows-Sysmon/Operational" | Add the event log to the logging service. |
sync-event-logs | Syncs the logging config. | |
remove-event-logs | "Microsoft-Windows-Sysmon/Operational" | Remove the event log from the logging service |
In this Article:
Armor Security Services
The tables within the sections below provide context to the Product and Operation fields used in the Schedule Task form.
