Install the AA Agent - Windows
This topic only applies to users who run:
Windows 2012
Windows 2012 R2
Windows 2016
Windows 2019
Before you begin, Armor recommends that you pre-installation information, including firewall rules. To learn more, see Armor Agent Pre-Installation.
Step 1: Locate the Armor Agent (AA)
Login to Nexus.
In the left-side navigation, hover over Infrastructure
 .
.Click on Compute, then click Virtual Machines.
Click on Add New VM.
Once on the Install an Anywhere Agent page:
Copy your license key — you’ll need this in a later step.
Select your operating system (Linux or Windows).
If you are using the Armor Management Portal (AMP):
Login to the Armor Management Portal (AMP).
In the left-side navigation, click Infrastructure.
Click Virtual Machines.
Hover over the plus ( + ) icon, and then click the Anywhere Agent icon
 .
. If you don't have any agents listed, then click Add an Armor Agent.
Once on the Install an Anywhere Agent page:
Copy your license key — you’ll need this in a later step.
Select your operating system (Linux or Windows).
Armor recommends installing the Armor Agent with all Security Services. Documentation on installing the Armor Agent only can be found below.
Step 2: Install the Armor Agent (AA)
NEW! Explore our new installer, designed for a smoother setup experience . Introducing a professional, cross-platform installer for the Armor Agent for Servers security solution.
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12;Invoke-WebRequest -Uri "https://agent.armor.com/latest/armor_installer_windows.exe" -OutFile "armor_installer.exe"; .\armor_installer.exe --license AAAA1-AAAA1-AAAA1-AAAA1-AAAA1 --region (region) -fullOR
Run the command to install the Armor Anywhere Agent with all Security Services.
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12; Invoke-WebRequest https://agent.armor.com/latest/armor_agent.ps1 -outfile armor_agent.ps1 ; .\armor_agent.ps1 -license AAAA1-AAAA1-AAAA1-AAAA1-AAAA1 -region (region) -fullYou must replace
AAAA1-AAAA1-AAAA1-AAAA1-AAAA1 with your specific license key
Currently, all users will leverage the region: us-west-armor
The Trend Recommendation Scan is not run upon installation, but is instead scheduled to run 10 minutes after installation and then every 7 days after that.
Step 3: Review the status of the Armor Agent (AA)
In Nexus, hover over Infrastructure
 and click on Compute.
and click on Compute.Then click Virtual Machines.
The Armor Agent column contains a colored status to indicate if the server's agent has registered a heartbeat to Armor.
A green
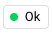 , status indicates the server's agent has registered a heartbeat in the past 4 hours.
, status indicates the server's agent has registered a heartbeat in the past 4 hours. A red
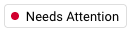 , status indicates the server's agent has not registered a heartbeat in the past 4 hours.
, status indicates the server's agent has not registered a heartbeat in the past 4 hours.
Then click on the corresponding Virtual Machine to see the VM’s detail page.
On the VM detail page, you can view information about the VM as well as the services installed on the server and their corresponding health.
The State column contains a color-coded status indicator to reflect the health of the listed service.
A green
 , status indicates the asset has communicated to Armor in the past 4 hours.
, status indicates the asset has communicated to Armor in the past 4 hours. A red
 , status indicates the asset has not communicated to Armor in the past 4 hours.
, status indicates the asset has not communicated to Armor in the past 4 hours. An orange
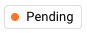 , status indicates the asset is pending registration or initialization.
, status indicates the asset is pending registration or initialization.The
 , status indicates the service is disabled; the customer has opted out of the service.
, status indicates the service is disabled; the customer has opted out of the service.
If you are using the Armor Management Portal (AMP):
In the Armor Management Portal (AMP), in the left-side navigation, click Infrastructure.
Click Virtual Machines
The State column contains a colored status to indicate if the server's agent has registered a heartbeat to Armor:
A green
 , status indicates the server's agent has registered a heartbeat in the past hour.
, status indicates the server's agent has registered a heartbeat in the past hour. A red
 ,status indicates the server's agent has not registered a heartbeat in the past hour.
,status indicates the server's agent has not registered a heartbeat in the past hour.
Then click on the corresponding VM.
On the VM detail page, you can view information about the VM as well as the services installed on the server and their corresponding health.
The State column contains a color-coded status indicator to reflect the health of the listed service.
A green status indicates the asset has communicated to Armor in the past hour.
A yellow status indicates the asset has not communicated to Armor in the past hour.
A gray status indicates the server's agent is pending registration or initialization.
An N/A status indicates the service is disabled; the customer has opted out of the service.
The State of each Armor Service will show Pending for two-hours after installation. After two hours, the State should accurately reflect the health of the service.
To access troubleshooting documentation for each Armor Security Service, click on the name of the service in the sub-agent health table.
Installing the Armor Agent for Servers (AA) Only
If you need to install the Armor Agent and Armor Security Services one by one, Armor recommends following the specific order outlined below to utilize the benefits of Recommendation Scans.
Recommendation Scans provide a good starting point for establishing a list of rules that you should implement for FIM and IPS. During a recommendation scan, the Armor Agent scans the operating system for installed applications, the Windows registry, open ports, and more. Recommendation Scans provide the rules and policies that will be auto applied by FIM and IPS, so auto apply features for those services must be turned on. Similarly, there is nothing for FIM and IPS to auto apply unless a Recommendation Scan is run.
If you do not want to run Recommendation Scans, please review the full list of CLI commands available here.
NEW! Explore our new installer, designed for a smoother setup experience . Introducing a professional, cross-platform installer for the Armor Agent for Servers security solution.
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12;Invoke-WebRequest -Uri "https://agent.armor.com/latest/armor_installer_windows.exe" -OutFile "armor_installer.exe"; .\armor_installer.exe --license AAAA1-AAAA1-AAAA1-AAAA1-AAAA1 --region (region)OR
Agent Only Step 1: Run the command to install the Armor Agent only.
[Net.ServicePointManager]::SecurityProtocol = [Net.SecurityProtocolType]::Tls12; Invoke-WebRequest https://agent.armor.com/latest/armor_agent.ps1 -outfile armor_agent.ps1 ; .\armor_agent.ps1 -license AAAA1-AAAA1-AAAA1-AAAA1-AAAA1 -region (region) You must replace
AAAA1-AAAA1-AAAA1-AAAA1-AAAA1 with your specific license key
Currently, all users will leverage the region: us-west-armor
Agent Only Step 2: Install Armor Security Services
Step 1: Install Trend
C:\.armor\opt\armor.exe trend installStep 2: Turn On File Integrity Monitoring in "Auto-Apply" Mode (This automatically applies FIM rules identified in Recommendation Scans. You must run a Recommendation Scan to identify the FIM rules that will be auto-applied.)
C:\.armor\opt\armor.exe fim on auto-apply-recommendations=onStep 3: Turn On Intrusion Prevention Service in "Auto-Apply" Mode (This automatically applies IPS rules identified in Recommendation Scans. You must run a Recommendation Scan to identify the IPS rules that will be auto-applied.)
Option 1: Detect Mode
C:\.armor\opt\armor.exe ips detect auto-apply-recommendations=onOption 2: Prevent Mode
C:\.armor\opt\armor.exe ips prevent auto-apply-recommendations=onStep 4: Turn on Malware Protection (Anti-Virus)
C:\.armor\opt\armor.exe av onStep 5: Install Vulnerability Scanning*
C:\.armor\opt\armor.exe vuln install*Vulnerability Scanning is a standalone service not included in the Trend Subagent
Step 6: Install Logging*
C:\.armor\opt\armor.exe logging install*Logging is a standalone service not included in the Trend Subagent
Step 7: Run a Recommendation Scan (This runs the initial Recommendation Scan to apply the baseline rules for FIM and IPS. Recommendations cannot be applied unless FIM and IPS are turned on and running in auto-apply mode.)
C:\.armor\opt\armor.exe trend recommendation-scanStep 8: Turn On Ongoing Recommendation Scans (This automatically runs Recommendation Scans every 7 days. All FIM and IPS rule changes are automatically applied if you followed Steps 2 and 3.)
C:\.armor\opt\armor.exe trend ongoing-recommendation-scan onAgent Only Step 3: Same as Step 3 in the full installation outline above.
Troubleshooting
The Armor Agent uses the BiosUUID to identify the hardware that the agent is running on. This number is tied to your motherboard (in the case of a physical computer) but is also present in a Virtual Machine.
In rare cases, the usual calls to retrieve this identifier fail to return this UUID, which will cause the Armor Agent to fail registration.
Turn on Armor Agent debug logging and try to register again. If the registration fails again, search the log for "Unable to get BiosUUID"
time="2020-07-24T03:06:48-05:00" level=debug msg="Unable to get BiosUUID"
time="2020-07-24T03:06:50-05:00" level=debug msg="Unable to get BiosUUID"In Windows, you can also try these commands to try to retrieve the UUID:
(in a Windows administrative-level cmd prompt:)
wmic csproduct get UUID(in Windows powershell:)
(Get-CimInstance -Class Win32_ComputerSystemProduct).UUIDAny of the above commands should return a 35byte string formatted like:
4C4C7544-0057-4C30-8046-C2C04F4C9132
The BIOS UUID is required by the Armor Agent, to ensure uniqueness of the device. The BIOS UUID must be readable by the operating system. If the BIOS UUID is not available to the operating system please check with your provider.
